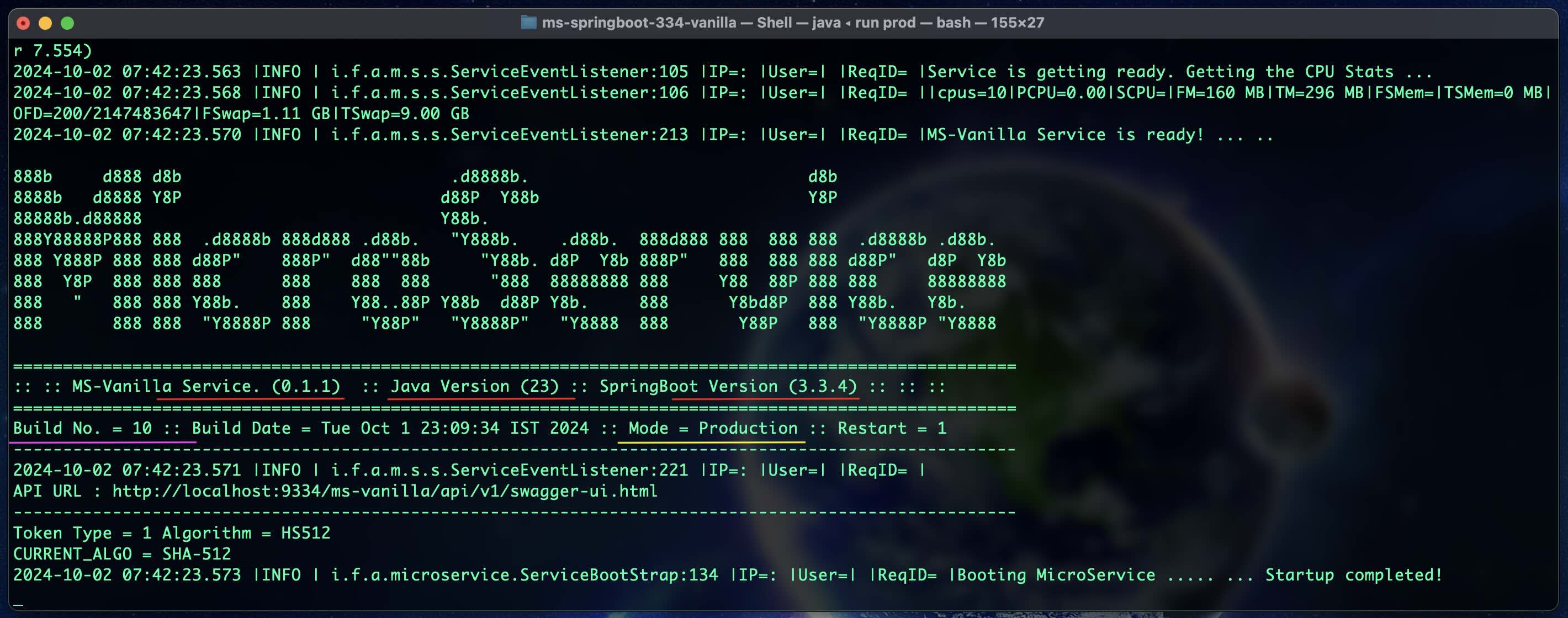
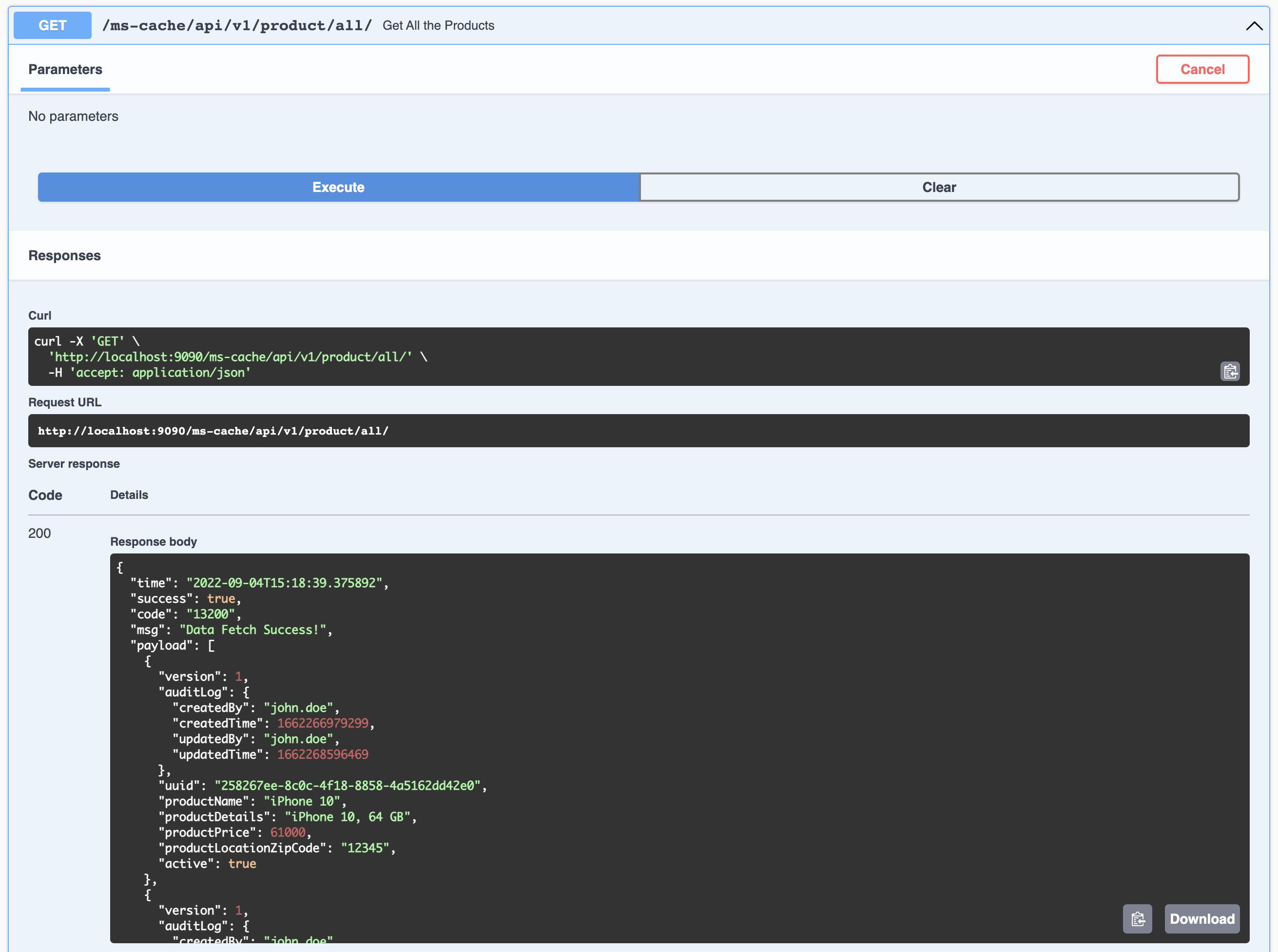
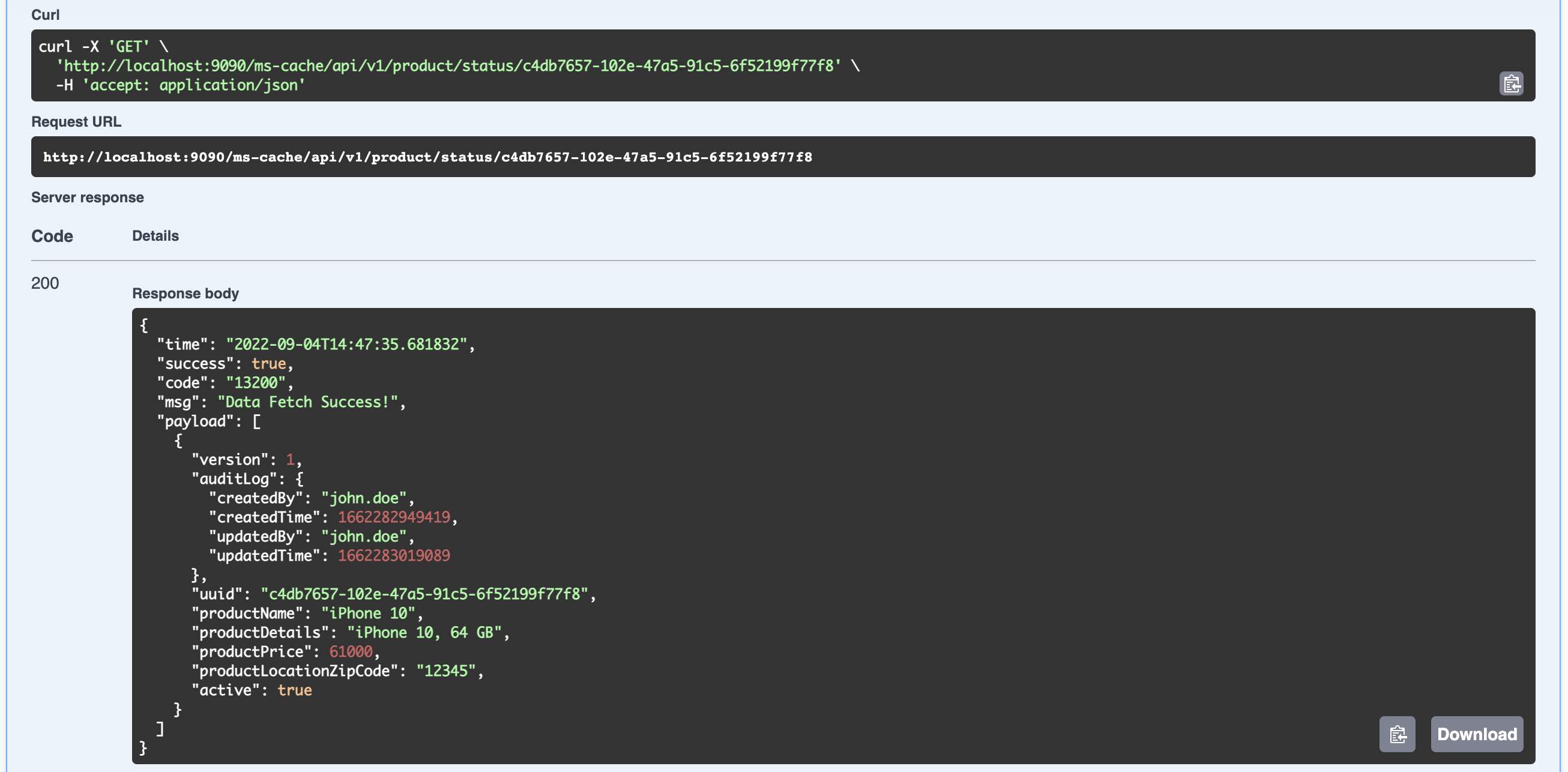
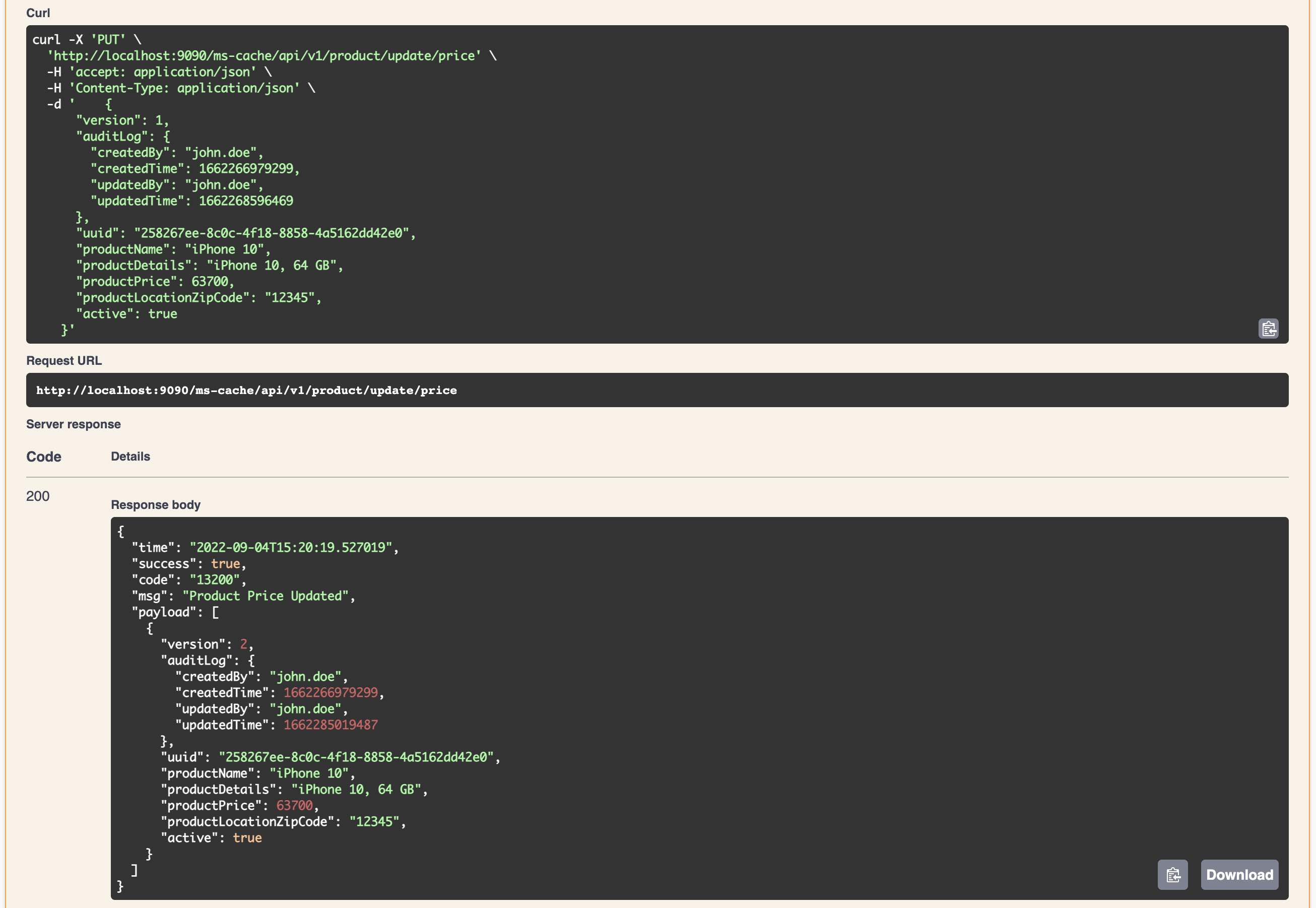
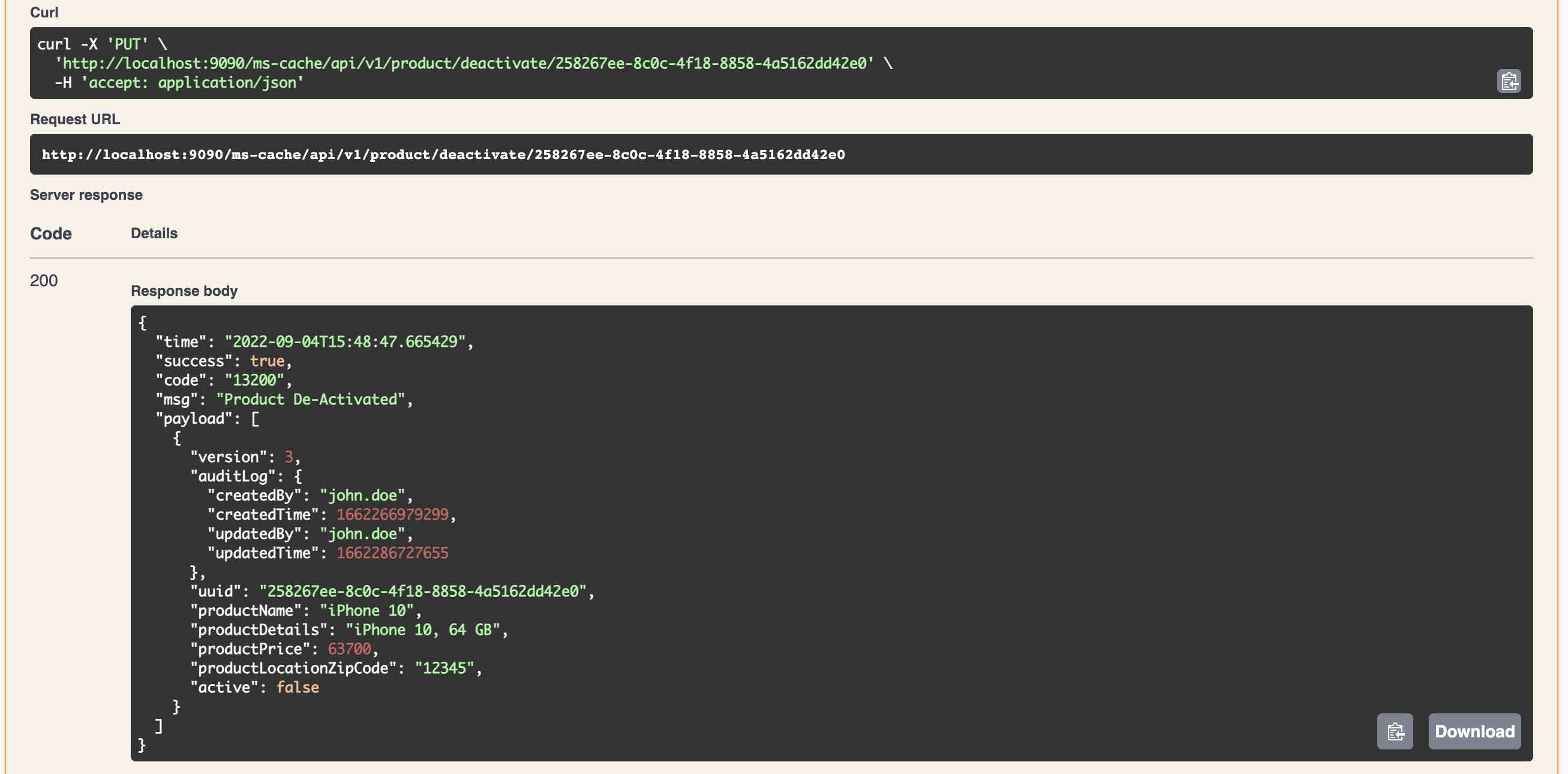
- Java 23
- SpringBoot 3.4.1
- Jakarta EE 10
Cloud-native (or microservice) architecture is an approach to application design in which software is broken down into small, independent services that communicate through lightweight APIs, enabling more agile development, scalability, and resilience. Rather than running a single monolithic codebase, each microservice can be developed, deployed, and scaled independently.
This decomposition—often containerized and orchestrated using tools such as Kubernetes—allows teams to quickly iterate on features, take advantage of cloud-native capabilities (like auto-scaling and automated deployments), and release updates with minimal disruption to the entire system. According to the Cloud Native Computing Foundation (CNCF), this approach fosters loosely coupled systems that are resilient, manageable, and observable, combined with robust automation (CNCF, 2023).
Key Features of Microservice (Sources: CNCF, 2023; Fowler, 2014):
- Service Independence: Each microservice is autonomous, allowing for separate development, deployment, and scaling without affecting others.
- Containerization: Services are commonly packaged in containers (e.g., Docker), providing consistency across different environments and efficient resource utilization.
- Lightweight Communication: Microservices communicate via lightweight protocols (often HTTP/REST or gRPC), reducing overhead and complexity.
- Scalability: Independent scaling of services ensures you can allocate resources exactly where needed, improving performance and cost-efficiency.
- Continuous Delivery and Deployment: Automation enables frequent, reliable releases to production while minimizing disruption.
- Resilience: Failure of one service doesn’t necessarily bring the entire system down, as microservices are loosely coupled and can handle faults gracefully.
References
- CNCF. (2023). What is Cloud Native? https://www.cncf.io/blog/2023/02/03/what-is-cloud-native/
- Fowler, M. (2014). Microservices. https://martinfowler.com/articles/microservices.html
- Security Auth/Authorization using AOP and Filters
- Exception Handling with Exception Framework using AOP ( ..microservice.adapters.aop)
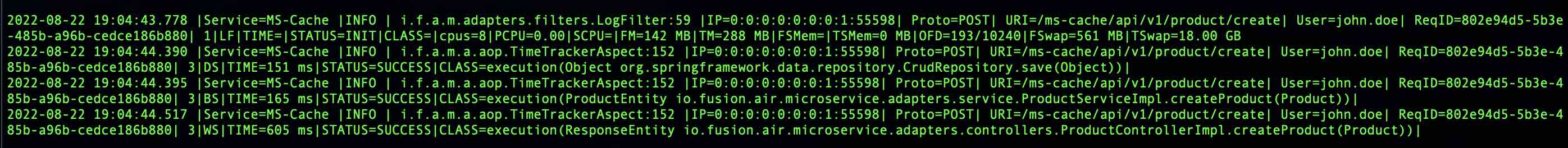
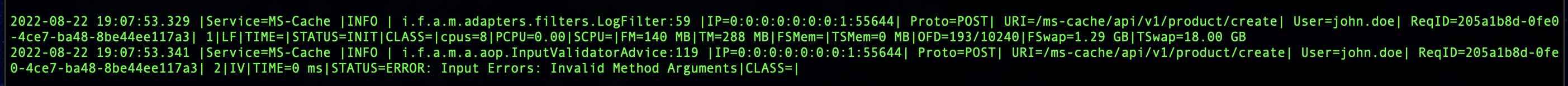
- Log Management using AOP (json and text formats) using Logback (...adapters.filters)
- Standardized REST Responses (...domain.models.StandardResponse)
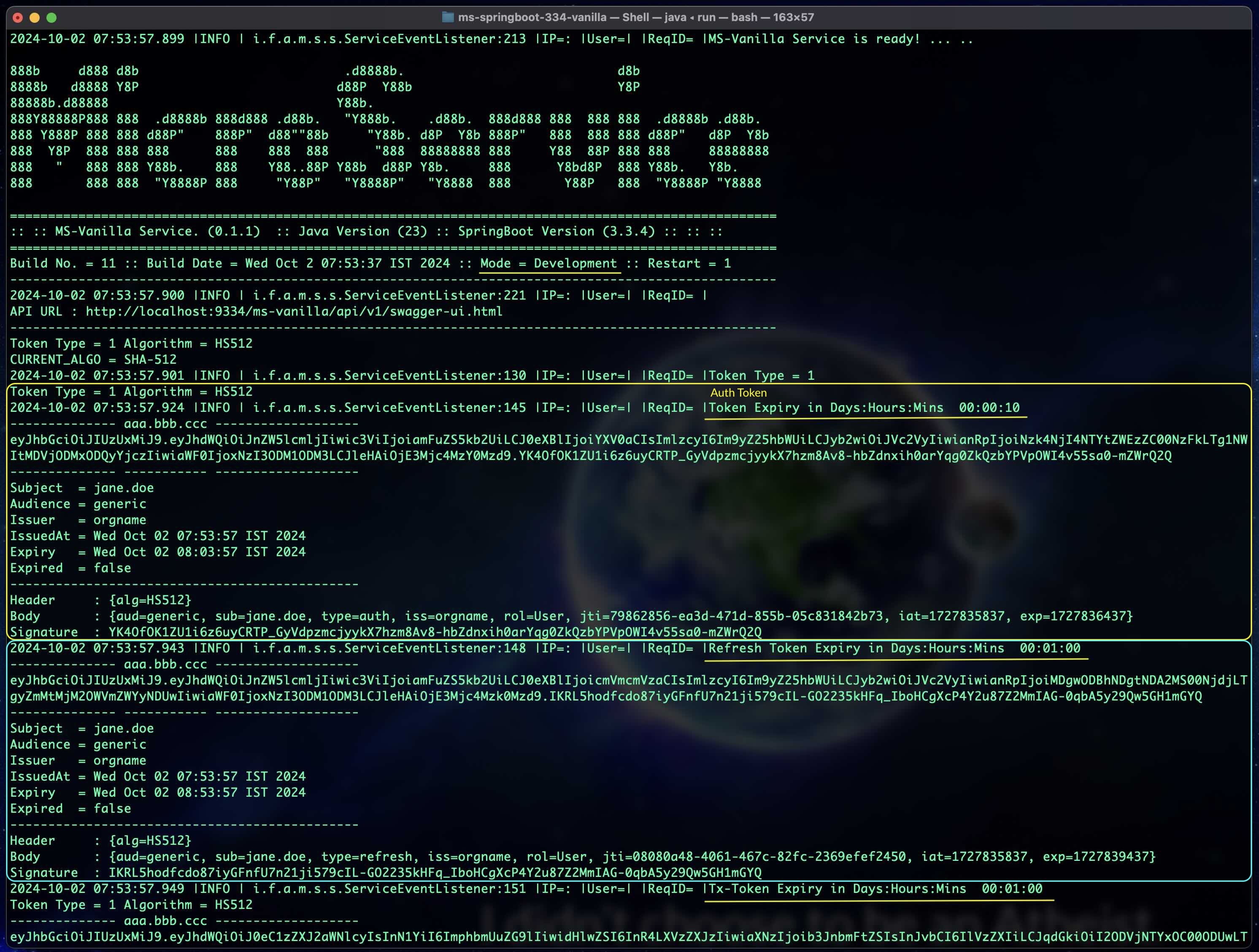
- Security using JWT Tokens / KeyCloak Auth (...microservice.adapters.security, ...microservice.security)
- Encrypting Sensitive Data using Encryption Algorithms (...microservice.security)
- JPA configurations for H2 and PostgreSQL (...server.config)
- Observability Using Micrometer, Prometheus and Open Telemetry.
- Database Password Encryption using Jasypt. Checkout the shell programs encrypt and decrypt.
- Digital Signatures using Standard Java Cryptography.
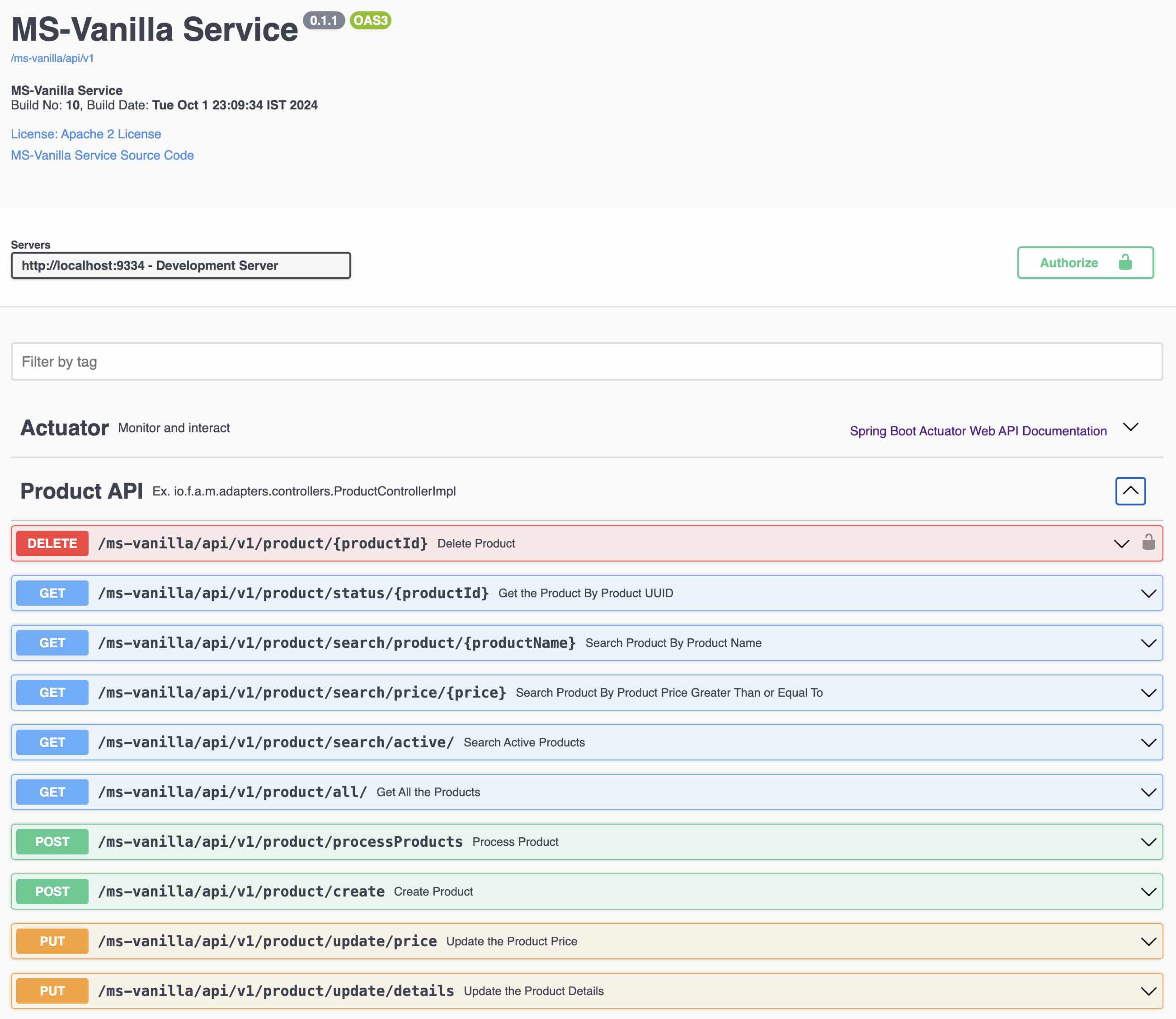
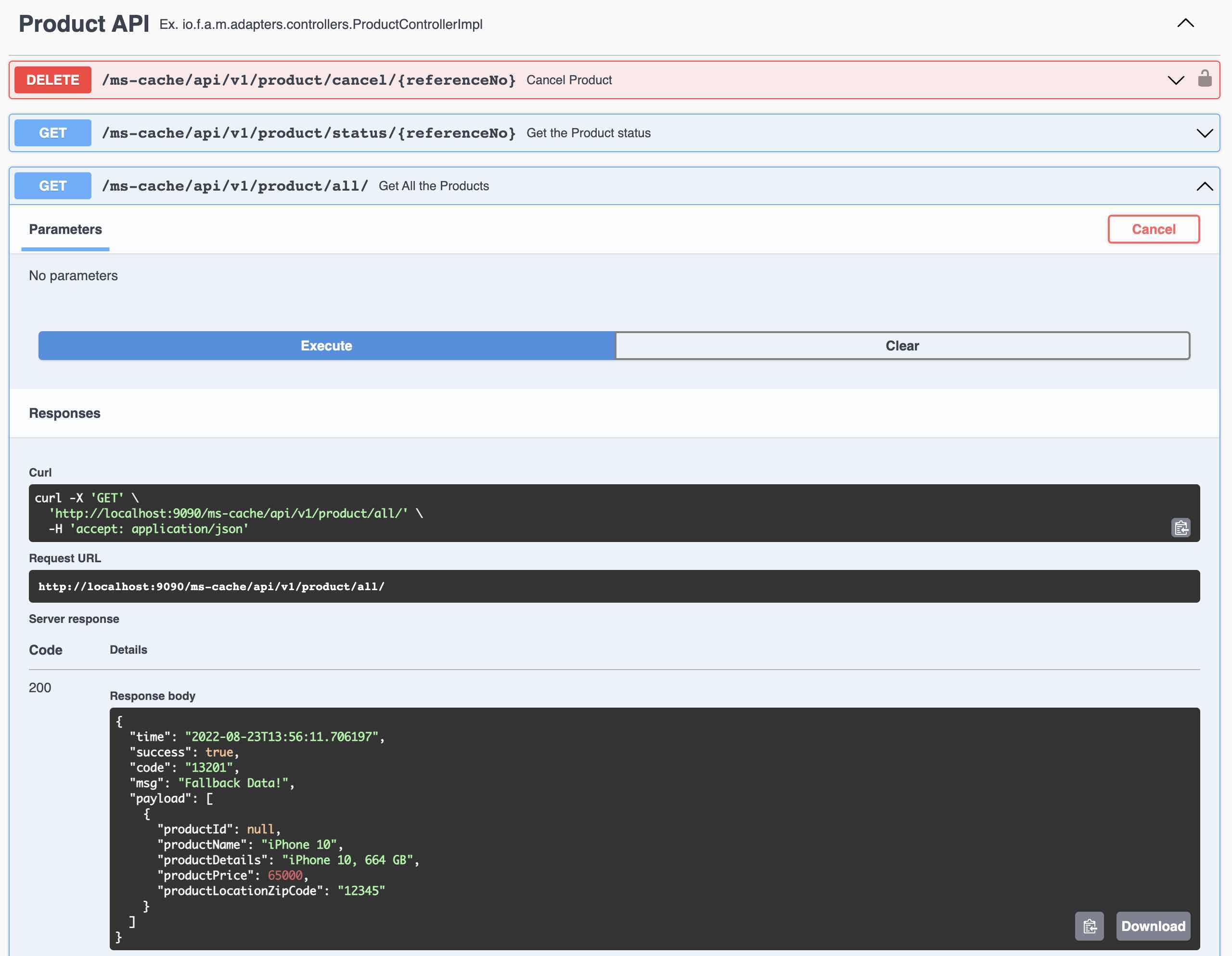
- Open API based Swagger API Docs (...microservice.adapters.controllers)
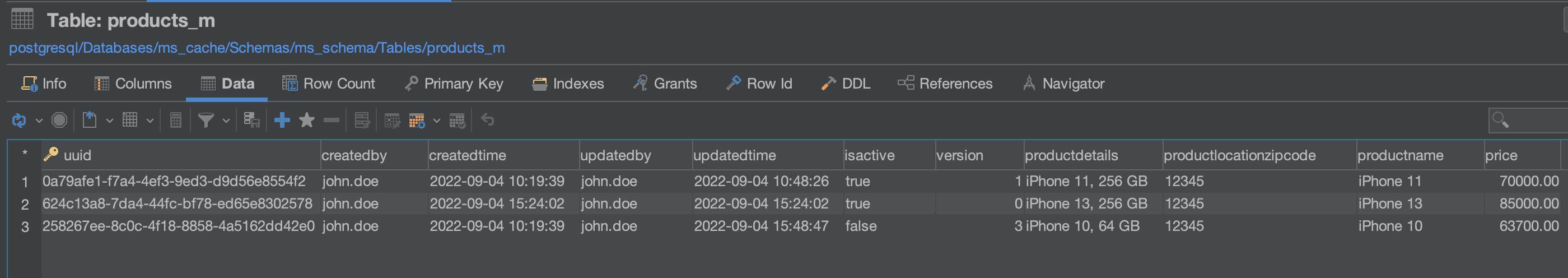
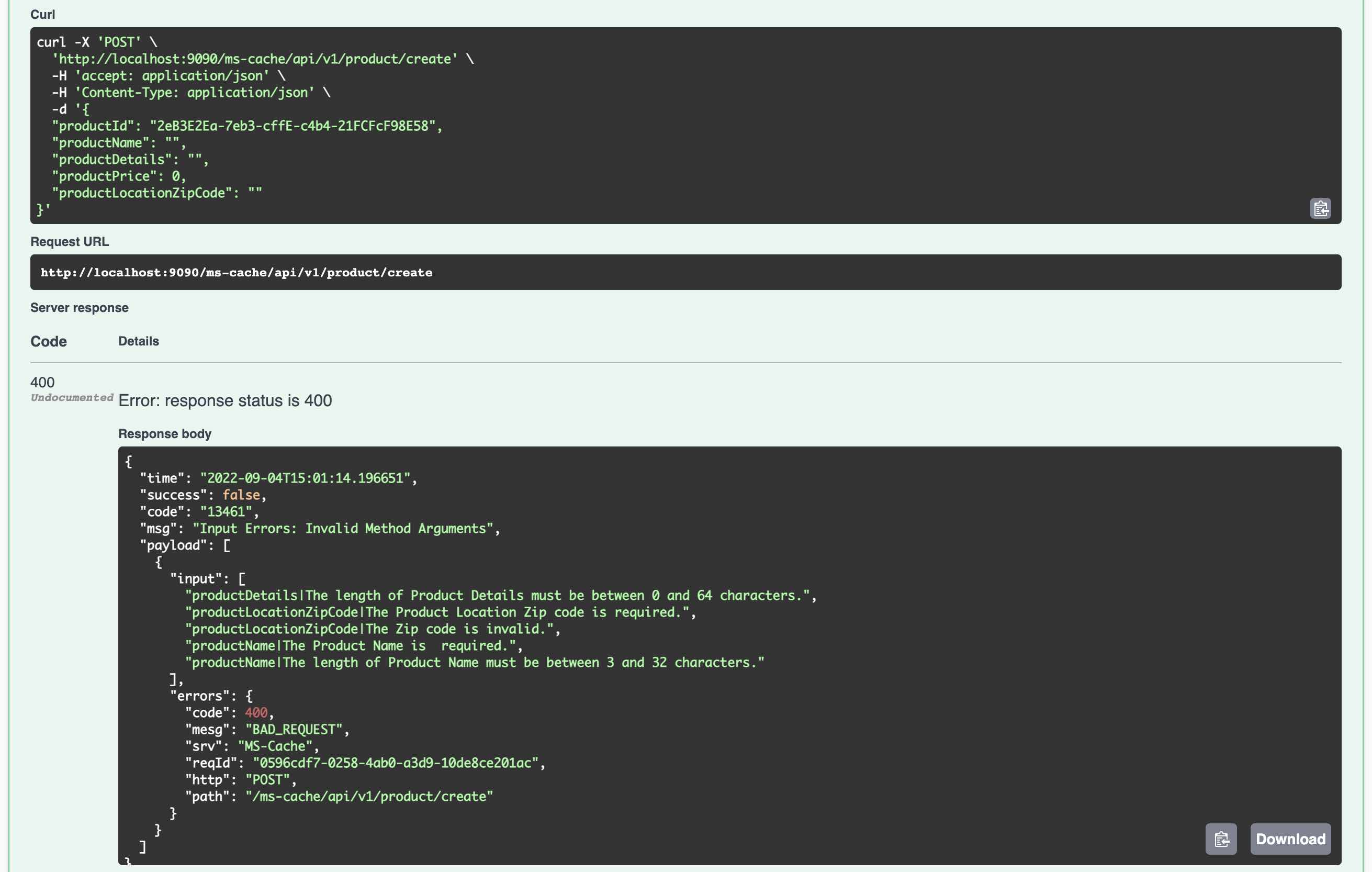
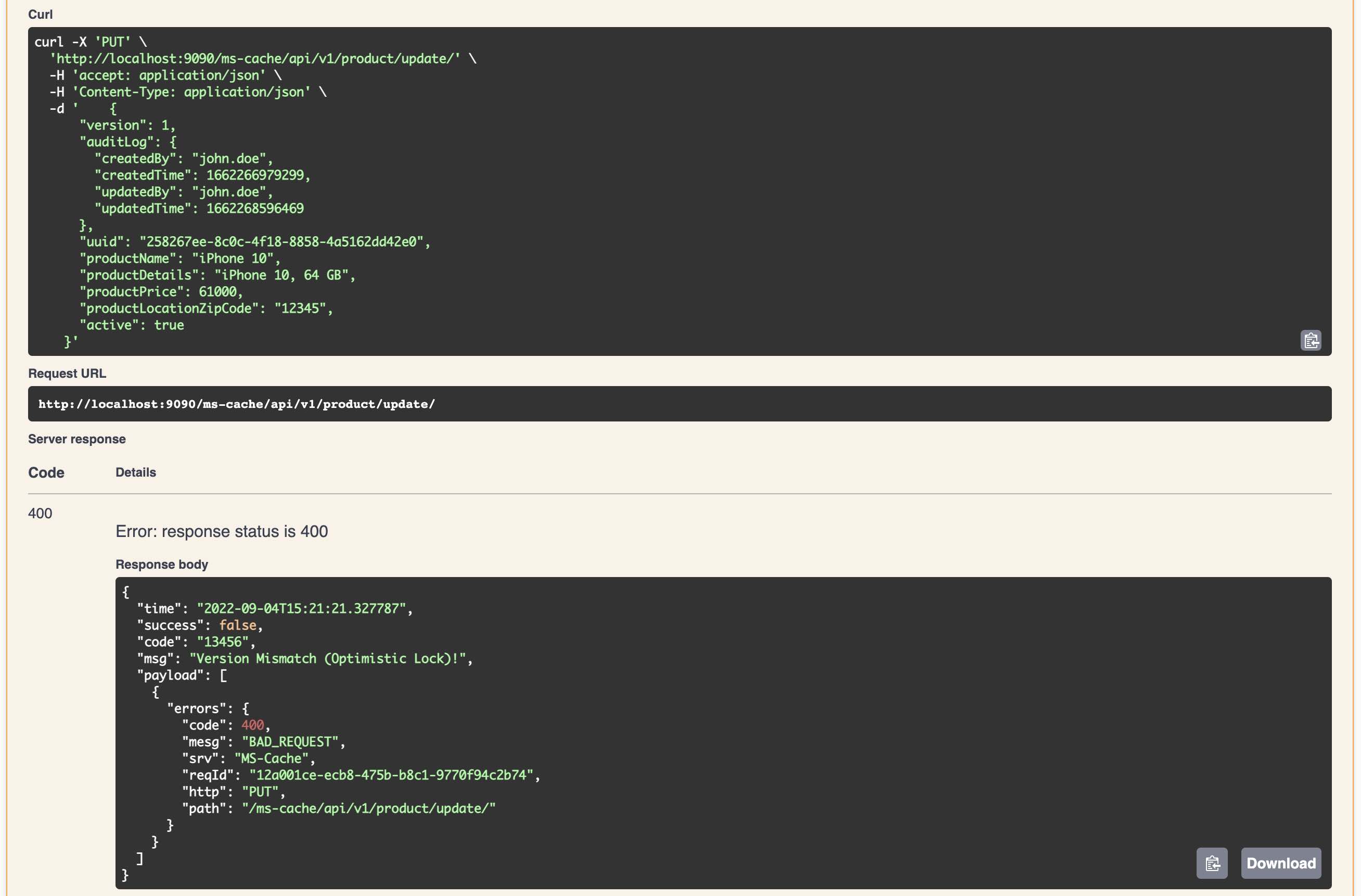
This microservice template offers a range of built-in functionalities. To simplify the demonstration of various features, an encrypted password is utilized for connecting to H2 and PostgreSQL databases. The template includes utilities for encrypting and decrypting passwords, ensuring that the encryption key is securely stored outside the application’s runtime context.
To know more about how to setup these passwords (for H2 & PostgreSQL) and environment variables checkout Session 1.2
Encrypted H2 (In Memory) Database Password. Uses H2 database in Dev (Profile) mode.
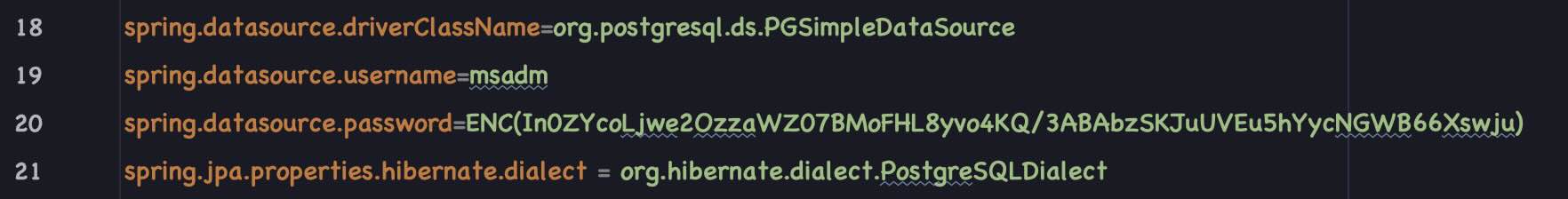
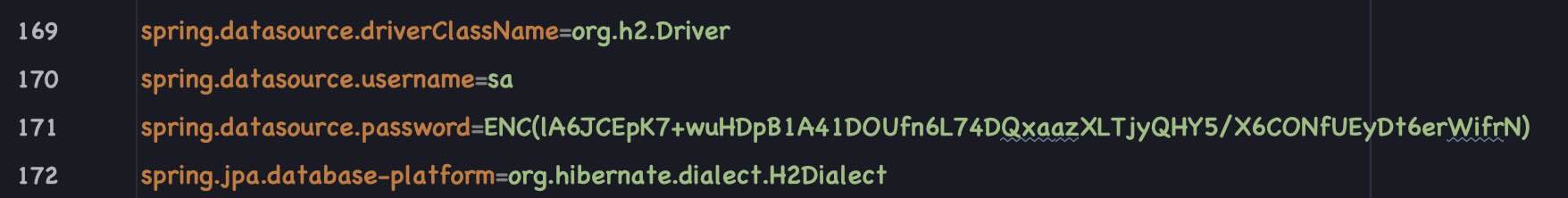 Encrypted PostgreSQL Database Password. Uses PostgreSQL DB in Staging & Prod (profile) mode.
Encrypted PostgreSQL Database Password. Uses PostgreSQL DB in Staging & Prod (profile) mode.
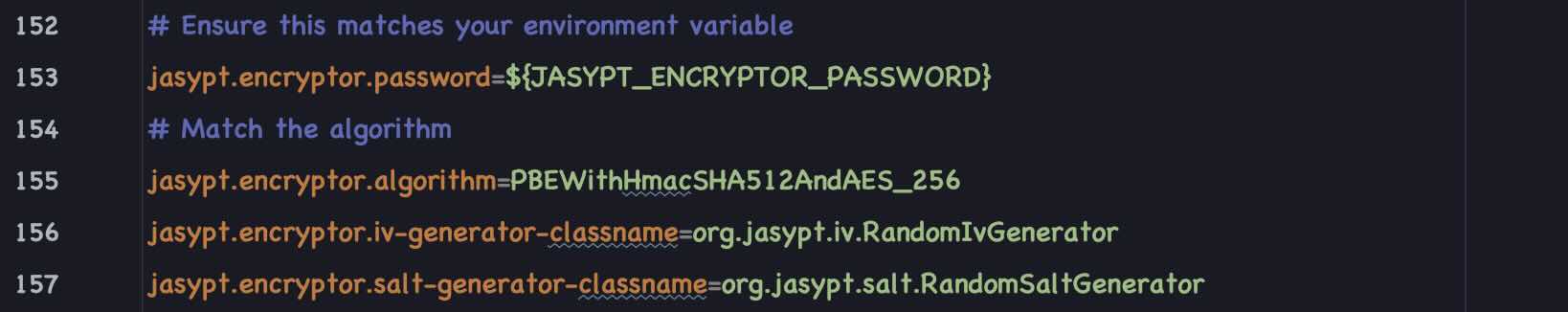
 Password can be decrypted only using an Encryption Key stored in System Enviornment variable
Password can be decrypted only using an Encryption Key stored in System Enviornment variable
If the Quality Gate check fails, it's because the password is encrypted within the application’s properties file, with the encryption key stored externally, outside the application’s context.
However, quality standards mandate that passwords should be securely stored in a vault, such as HashiCorp Vault, for enhanced security.
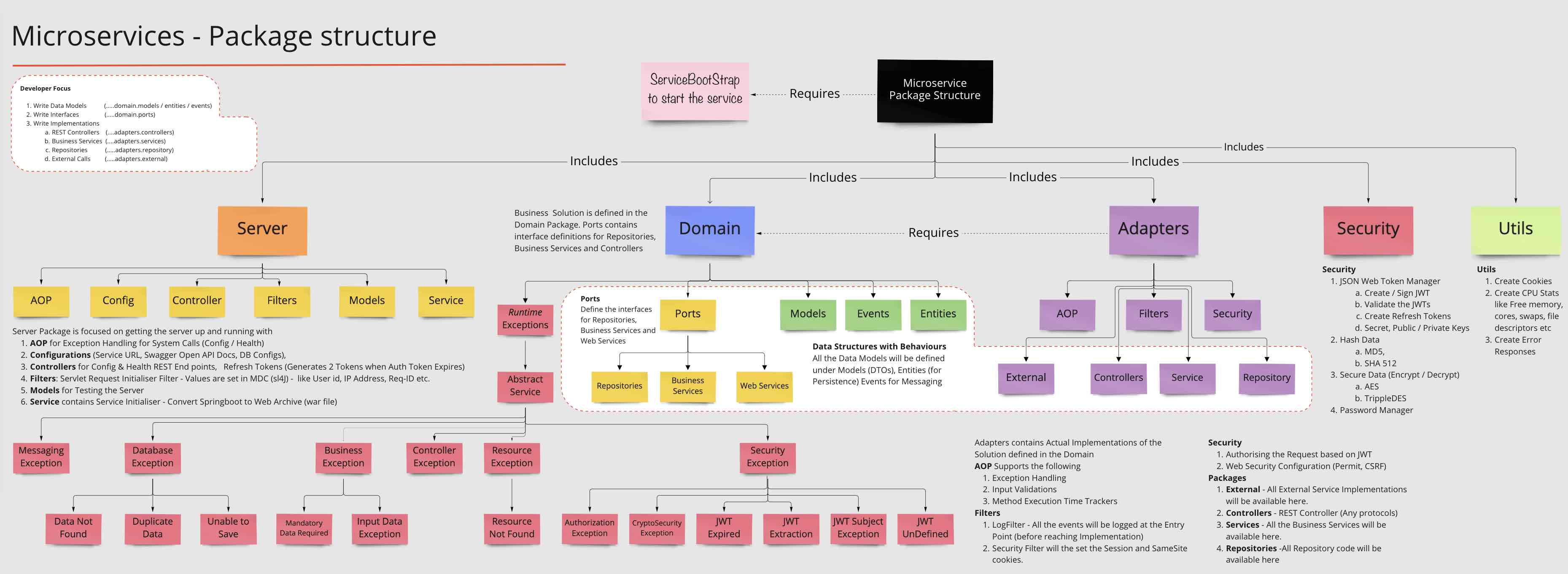
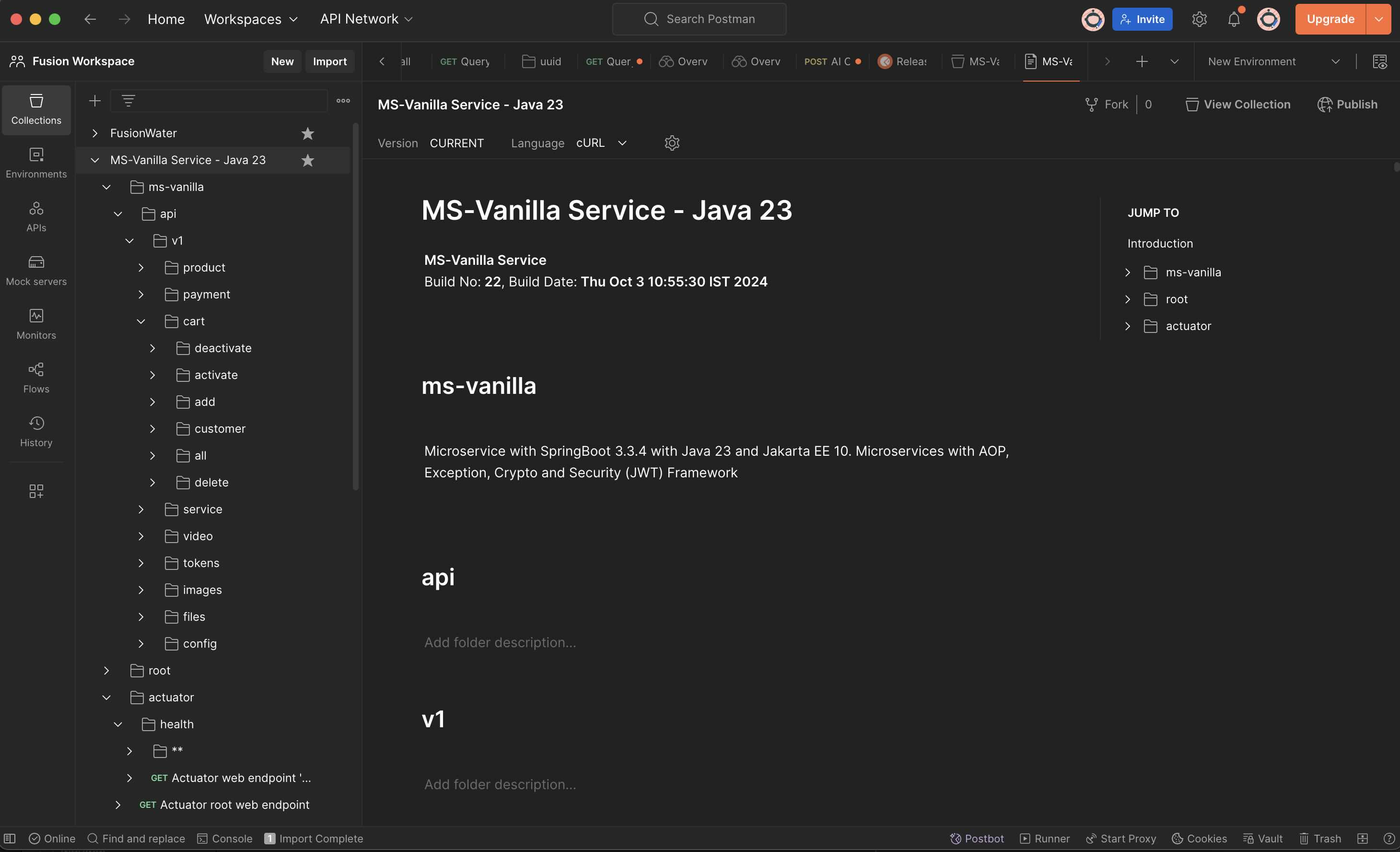
io.fusion.air.microservice
- adapters (All the Implementations from App/Service perspective)
- domain (All Entities, Models, Interfaces for the implementations)
- security (All Security related modules)
- server (Managing the Service - from a server perspective, Setups (Cache, DB, Kafka etc, Configs)
- utils (Standard Utilities)
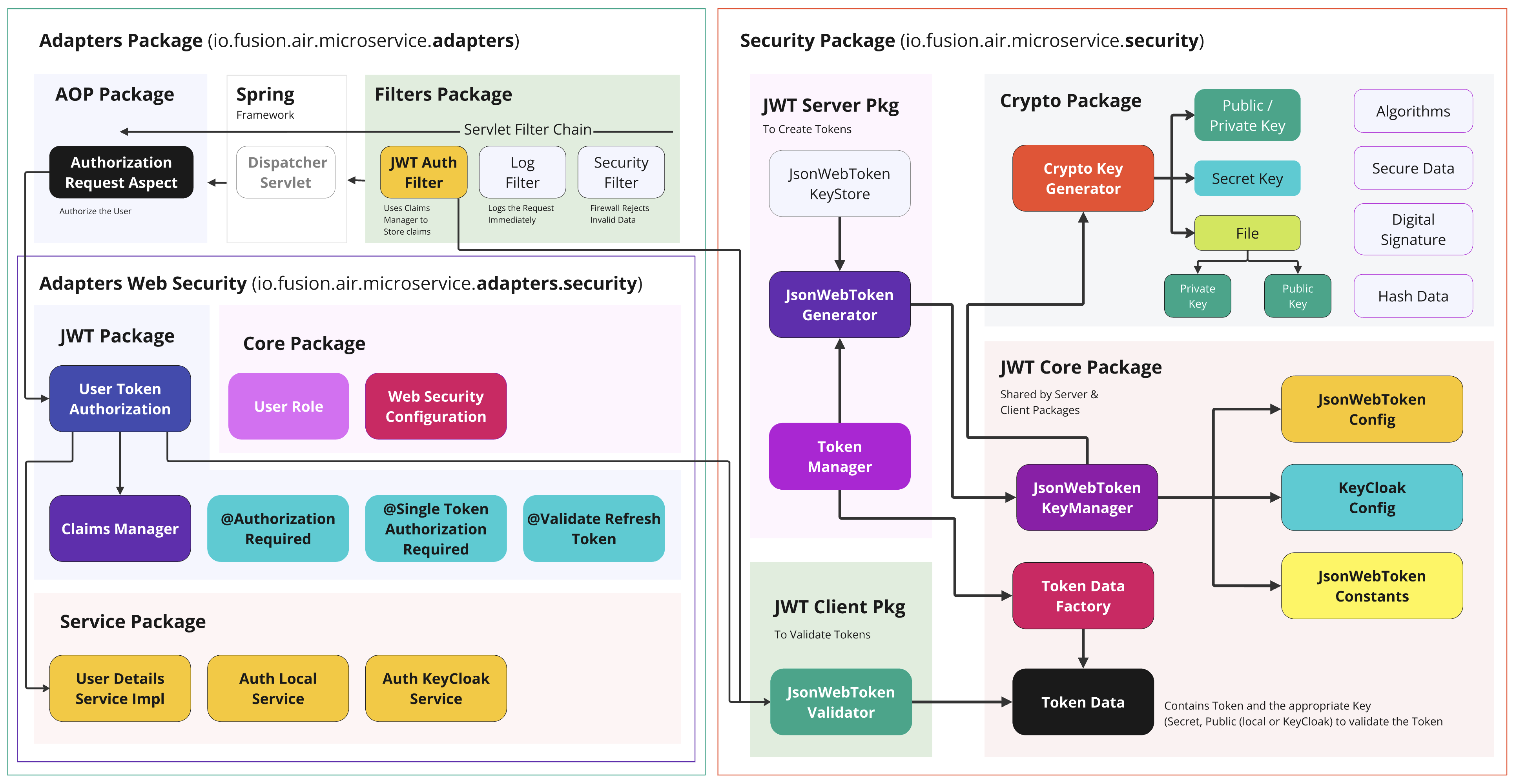
- Adapters Package (left side) – Integrations with Spring MVC, AOP, Filters, and Web Security.
- Security Package (right side) – Core libraries and utilities for JWT creation, validation, cryptography, etc.
A. Filters Package
- JWT Auth Filter
- A javax.servlet.Filter (or jakarta.servlet.Filter) that intercepts requests early in the servlet chain.
- It extracts JWTs from headers, validates or parses them, and stores user claims in a ClaimsManager for downstream use.
- Log Filter
- Another servlet filter for logging requests. Possibly logs details like request URIs, IP addresses, timings, etc.
- Security Filter
- A filter that enforces security rules at the servlet layer (e.g., blocking requests with invalid data or applying firewall rules).
- Complements or replaces Spring Security’s default filter chain in some scenarios. These filters run before the DispatcherServlet. They can reject or manipulate requests if authentication or security checks fail.
B. Spring Framework (DispatcherServlet)
- DispatcherServlet is the central Spring MVC component that routes incoming HTTP requests to the appropriate controller endpoints. Checkout the API flow in Part 4 of my Java 23 series.
C. AOP Package
- Authorization Request Aspect
- A Spring AOP aspect that intercepts controller or service methods to enforce authorization rules.
- Typically checks whether the user has the necessary roles/permissions based on JWT claims or custom annotations (@AuthorizationRequired).
Checkout the Java 23, SpringBoot 3.3.4, & Jakarta EE 10 for more details on this topic.
- Java 23, SpringBoot 3.3.4 & Jakarta 10 — Part 1
- Java 23, SpringBoot 3.3.4: AOP Exception Handling — Part 2
- Java 23, SpringBoot 3.3.4: Logback Setup — Part 3
- Java 23, SpringBoot 3.3.4: Log/Events: API Flow & Logging — Part 4
- Java 23, SpringBoot 3.3.4: Metrics: Micrometer, Prometheus, Actuator — Part 5
- Java 23, SpringBoot 3.3.4: Metrics: Micrometer & AOP — Part 6
- Java 23, SpringBoot 3.3.4: Tracing: OpenTelemetry — Part 7
- Java 23, SpringBoot 3.4.1: Tracing: OpenTelemetry In Action — Part 8 Coming Soon
- Java 23, SpringBoot 3.4.1: Filters: Security, Log — Part 9 Coming Soon
- Java 23, SpringBoot 3.4.1: AOP: Spring Security — Part 10 Coming Soon
- Java 23, SpringBoot 3.4.1: CRUD — Part 11 Coming Soon
- Java 23, SpringBoot 3.4.1: CRUD Queries & Page Sort — Part 12 Coming Soon
- SpringBoot 3.3.4
- Java 23
- Jakarta EE 10 (jakarta.servlet., jakarta.persistence., javax.validation.*)
- Maven 3.8.6
- Git 2.31
- git clone https://github.com/arafkarsh/ms-springboot-334-vanilla
- cd ms-springboot-334-vanilla
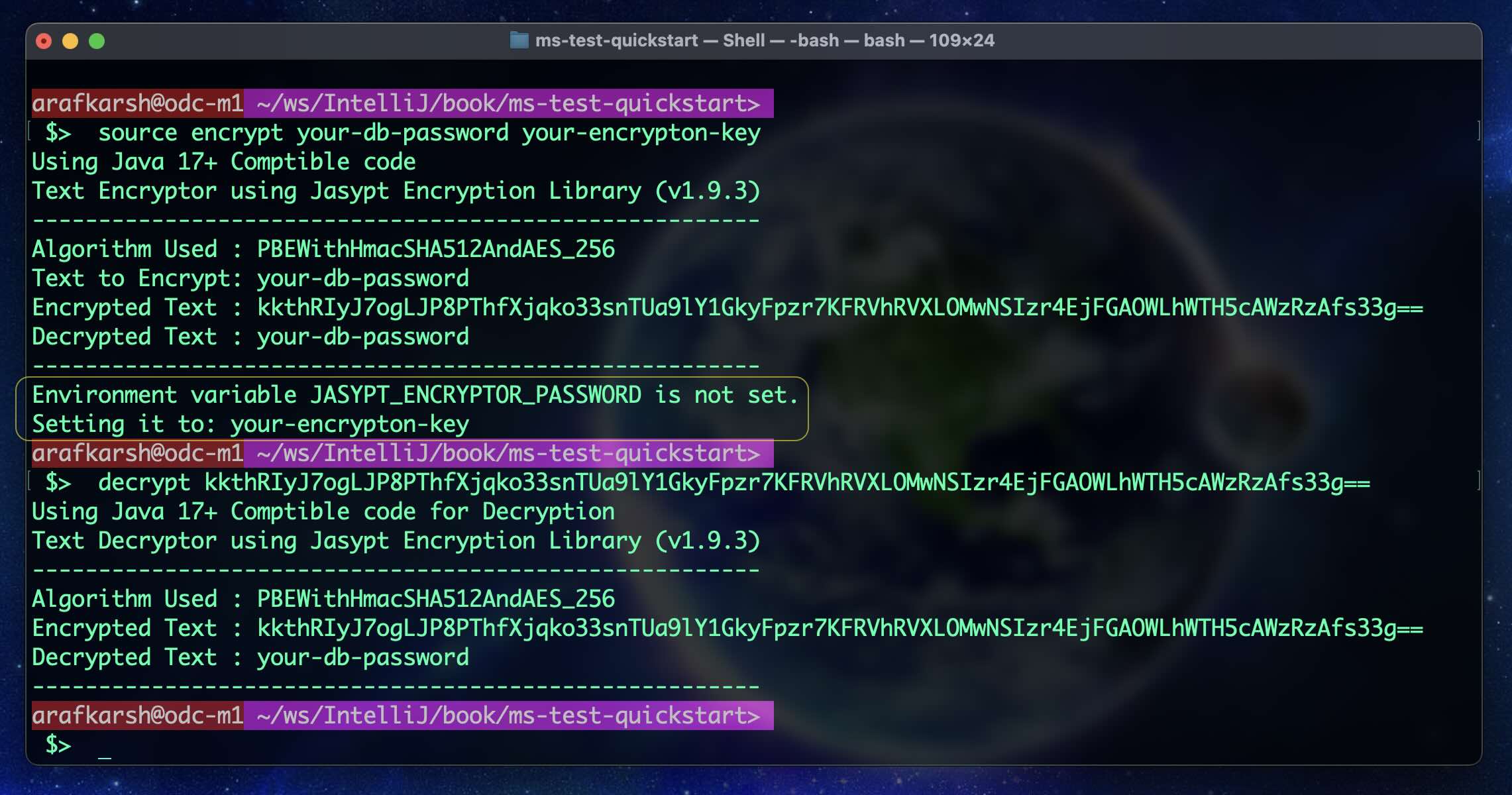
If you dont encrypt the password with your Encryption Key it will throw an exception saying unable to decrypt the password. Here are the steps to encrypt the password.
Run the follwing command line option
$ source encrypt your-db-password your-encrypton-key
Your encryption key will be set in the following Environment variable. SpringBoot Will automatically pickup the encryption key from this environment variable.
JASYPT_ENCRYPTOR_PASSWORD=your-encrypton-key
Update the property file in the local file
spring.datasource.password=ENC(kkthRIyJ7ogLJP8PThfXjqko33snTUa9lY1GkyFpzr7KFRVhRVXLOMwNSIzr4EjFGAOWLhWTH5cAWzRzAfs33g==)
AND
- the property template in src/main/resources/app.props.tmpl
- dev src/main/resources/application-dev.properties
spring.datasource.password=ENC(kkthRIyJ7ogLJP8PThfXjqko33snTUa9lY1GkyFpzr7KFRVhRVXLOMwNSIzr4EjFGAOWLhWTH5cAWzRzAfs33g==)
AND the property files for
- staging src/main/resources/application-staging.properties
- prod src/main/resources/application-prod.properties
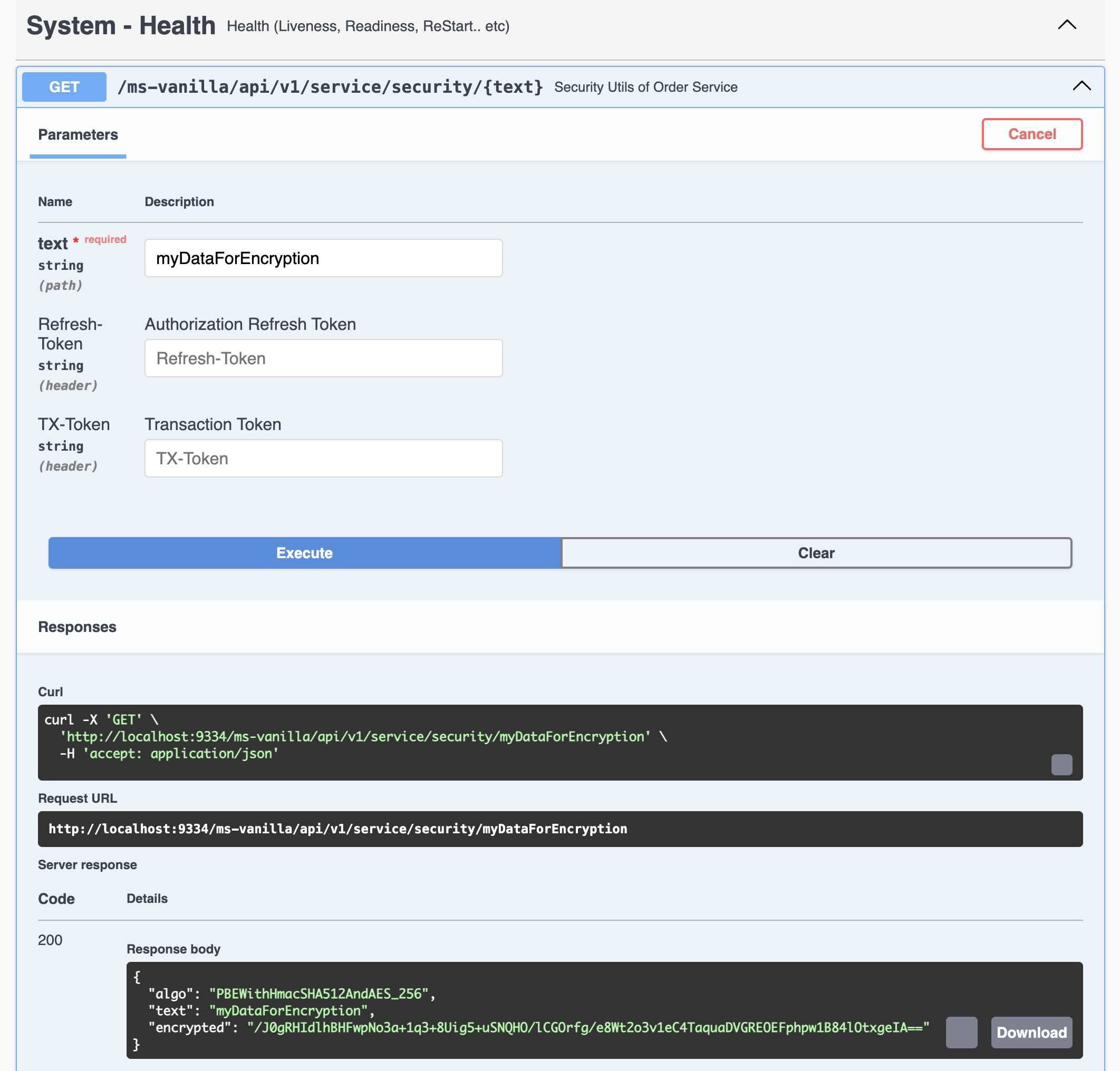
spring.datasource.password=ENC(/J0gRHIdlhBHFwpNo3a+1q3+8Uig5+uSNQHO/lCGOrfg/e8Wt2o3v1eC4TaquaDVGREOEFphpw1B84lOtxgeIA==)
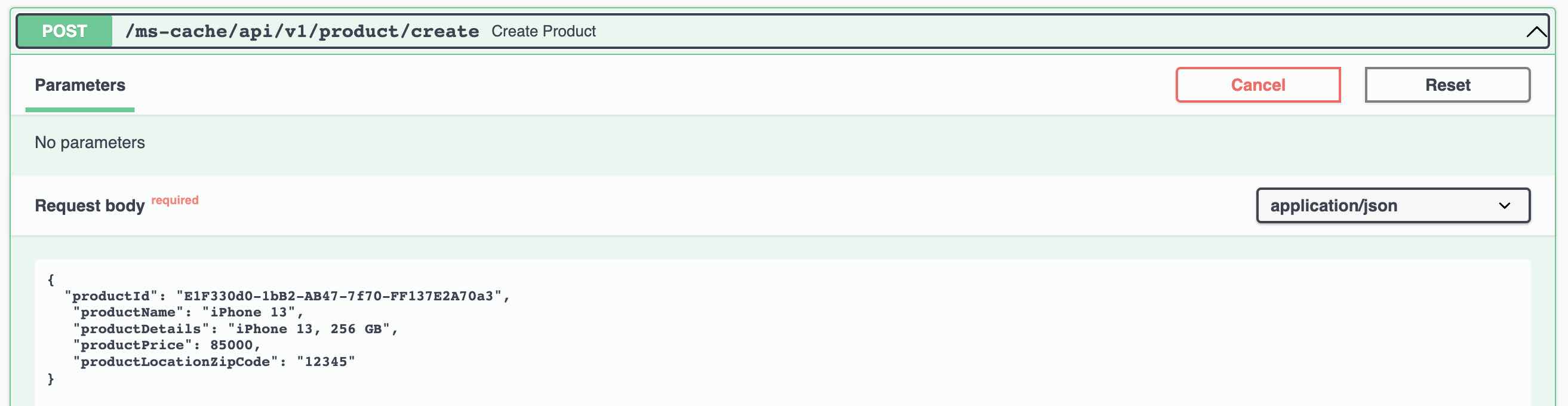
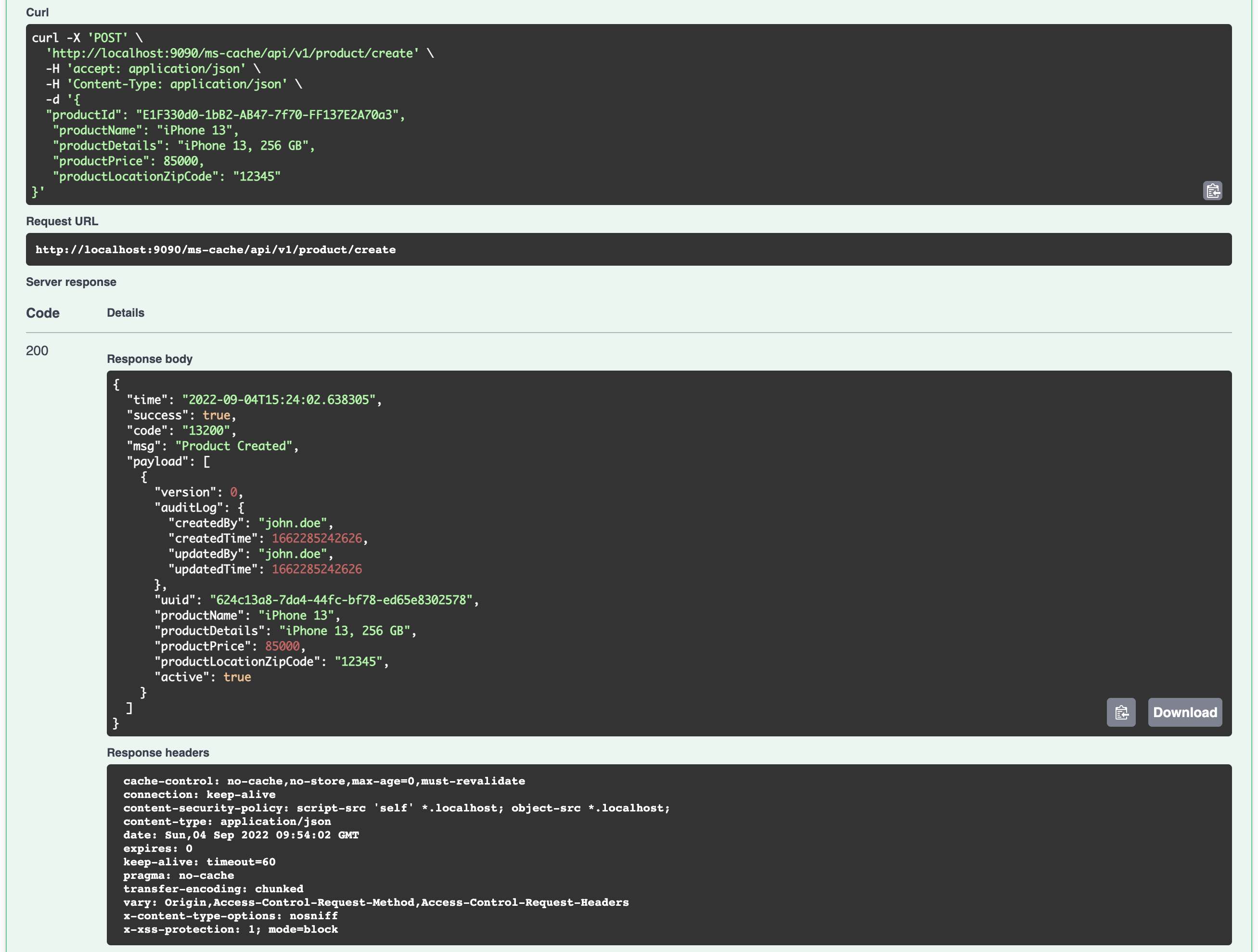
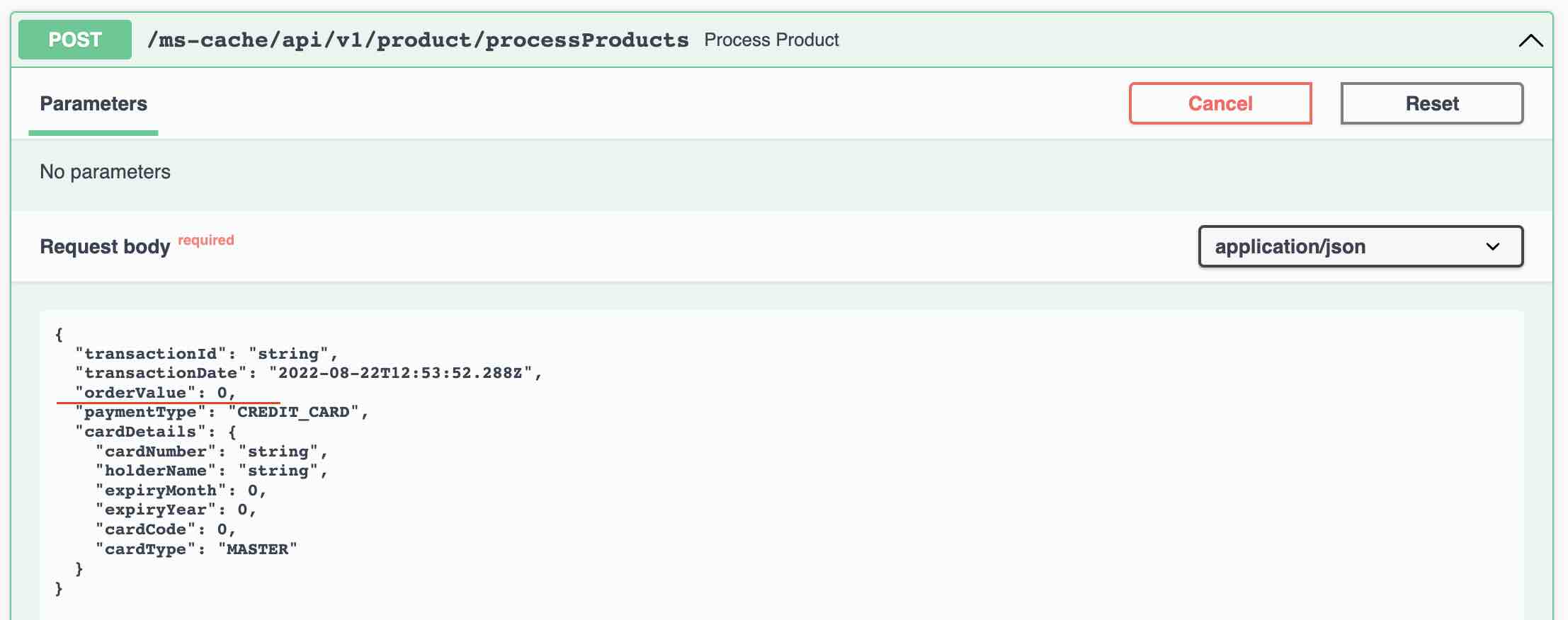
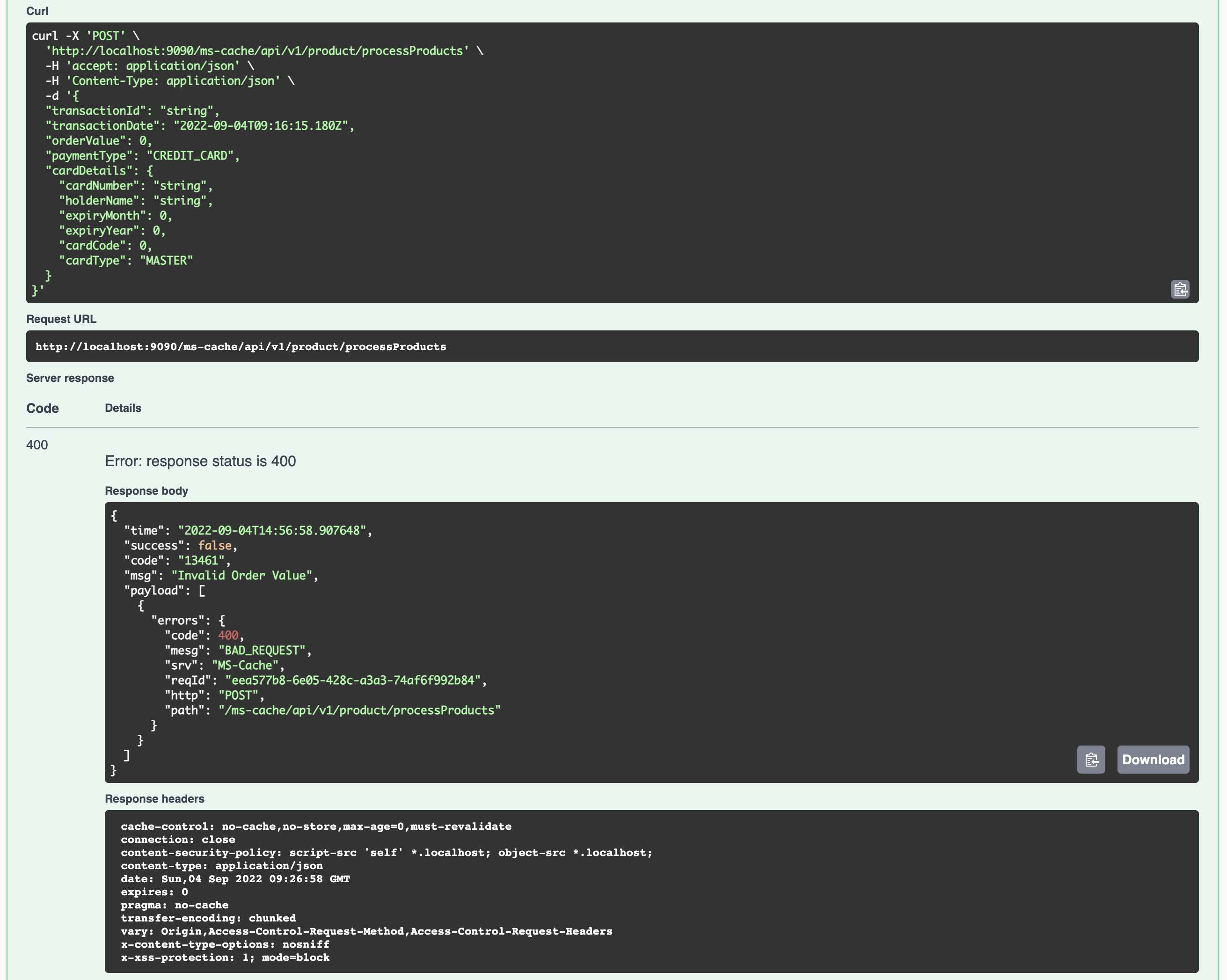
You can use the following REST Endpoint to encrypt the sensitive data. This will work only after setting the environment variable JASYPT_ENCRYPTOR_PASSWORD and creating the first DB password using the command line options.
Execute the "compile" from ms-springboot-334-vanilla
- compile OR ./compile (Runs in Linux and Mac OS)
- mvn clean; mvn -e package; (All Platforms)
- Use the IDE Compile options
- Clean up the target folder
- Generate the build no. and build date (takes application.properties backup)
- build final output SpringBoot fat jar and maven thin jar
- copy the jar files (and dependencies) to src/docker folder
- copy the application.properties file to current folder and src/docker folder
In Step 1.3.2 application.properties file will be auto generated by the "compile" script. This is a critical step. Without generated application.properties file the service will NOT be running. There is pre-built application properties file. Following three property files are critical (to be used with Spring Profiles)
- application.properties
- application-dev.properties
- application-staging.properties
- application-prod.properties
- dev (Development Mode)
- staging (Staging Mode)
- prod (Production Mode)
- Linux or Mac OS - Profiles (dev, staging, or prod)
run
run dev
run staging
run prod
- All Platforms - Profiles (dev, staging, or prod)
mvn spring-boot:run -Dspring-boot.run.profiles=dev
mvn spring-boot:run -Dspring-boot.run.profiles=staging
mvn spring-boot:run -Dspring-boot.run.profiles=prod
- Microsoft Windows - Profiles (dev, staging, or prod)
java -jar target/ms-vanilla-service-*-spring-boot.jar --spring.profiles.active=dev -Djava.security.manager=java.lang.SecurityManager -Djava.security.policy=./vanilla.policy
java -jar target/ms-vanilla-service-*-spring-boot.jar --spring.profiles.active=staging -Djava.security.manager=java.lang.SecurityManager -Djava.security.policy=./vanilla.policy
java -jar target/ms-vanilla-service-*-spring-boot.jar --spring.profiles.active=prod -Djava.security.manager=java.lang.SecurityManager -Djava.security.policy=./vanilla.policy
- test OR ./test (Runs in Linux or Mac OS)
- Execute the curl commands directly (from the test script)
Check the application.properties (in the project root directory) to change the profile Ex. spring.profiles.default=dev
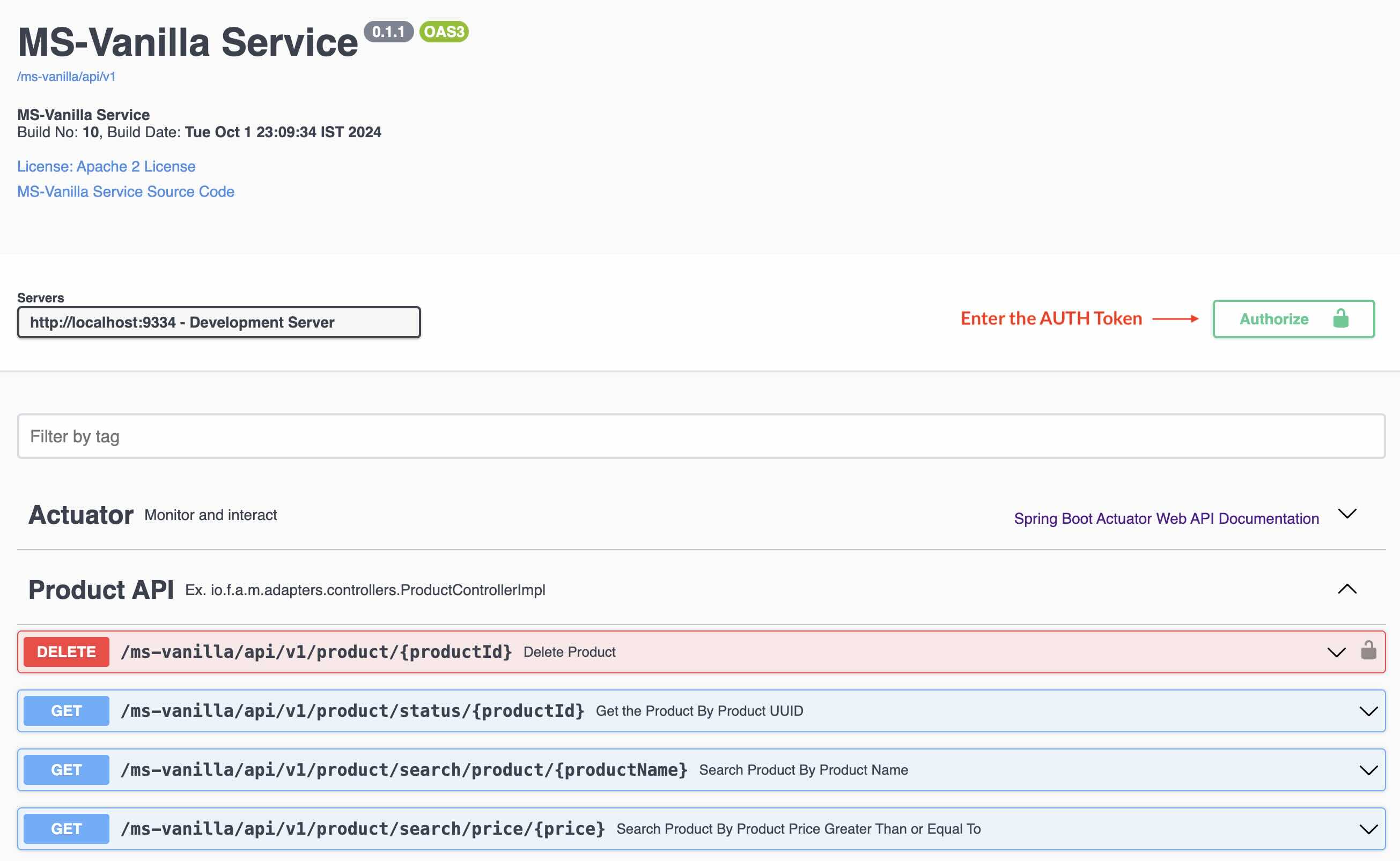
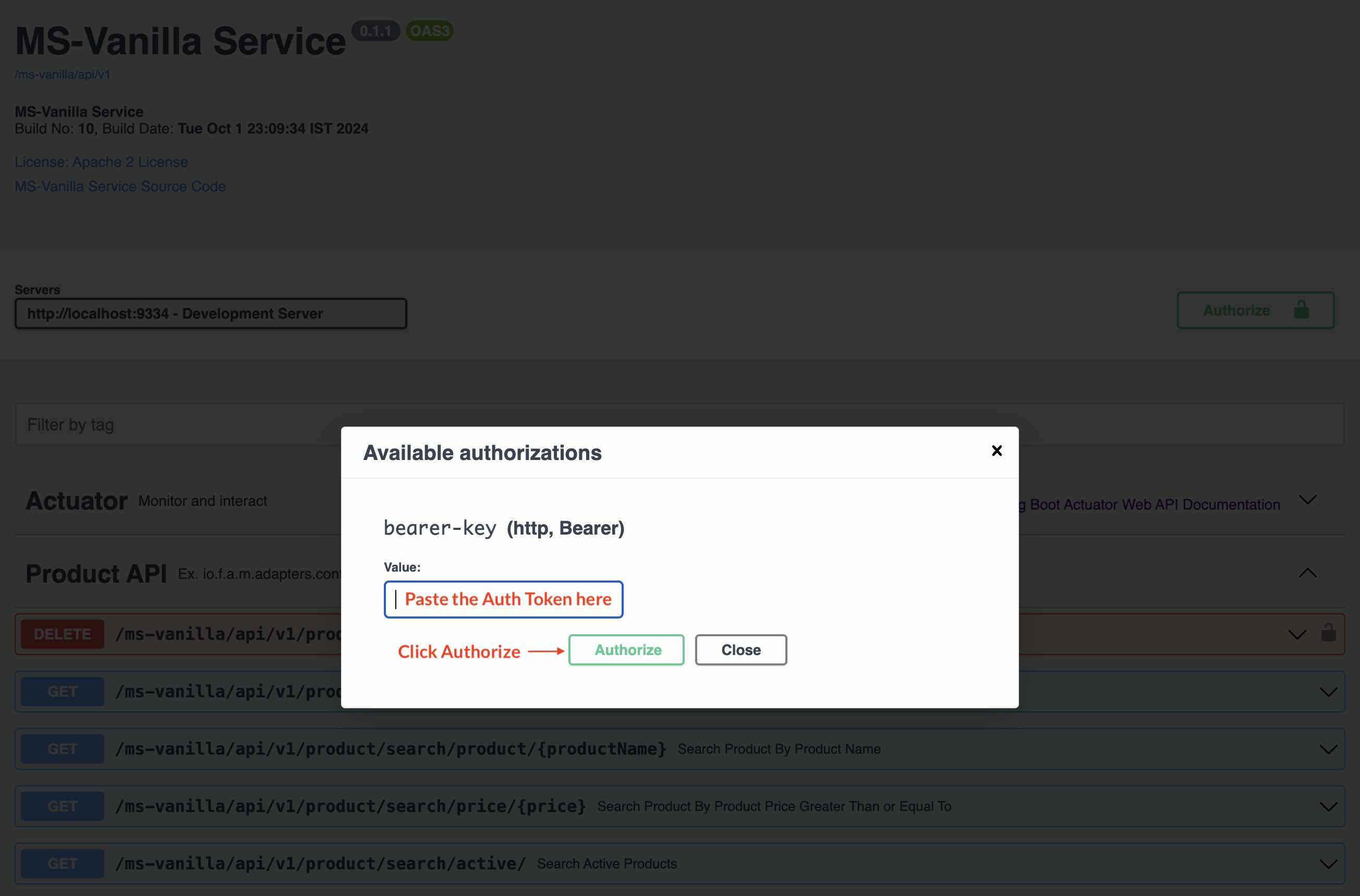
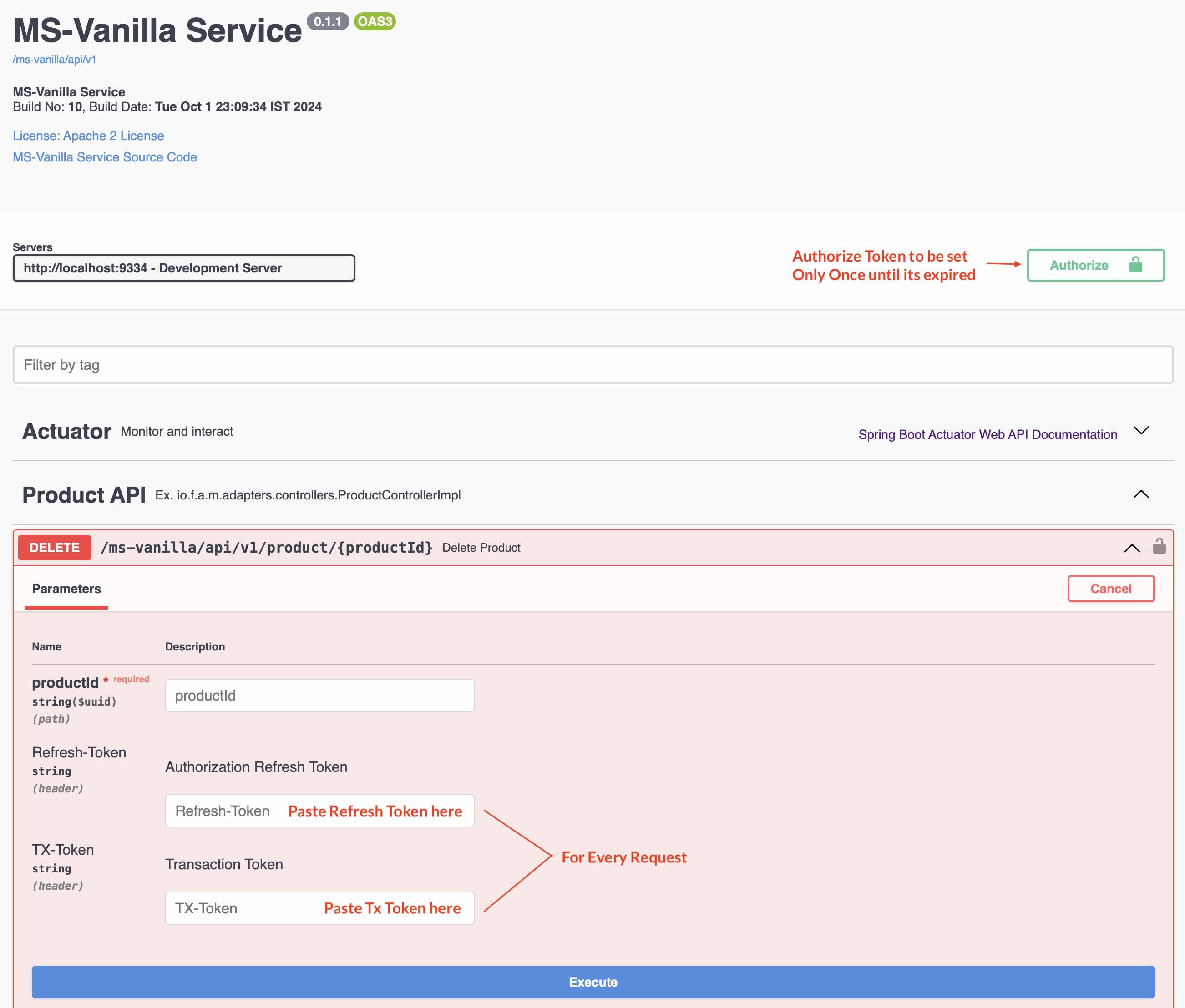
To test the APIs (in secure mode - you will see a lock icon in the Swagger Docs). These test tokens are generated based on the flag server.token.test=true in the application.properties file. (Change the app.props.tmpl if you want to change in the build process.) In the Production environment, this flag should be false. These tokens can be generated only in an Auth Service. All the services need not generate these tokens unless for the developers to test it out. In a real world scenario, disable (Comment out the function generateTestToken() from the code java file ServiceEventListener.java in the package documentation io.fusion.air.microservice.server.service) this feature for production environment.
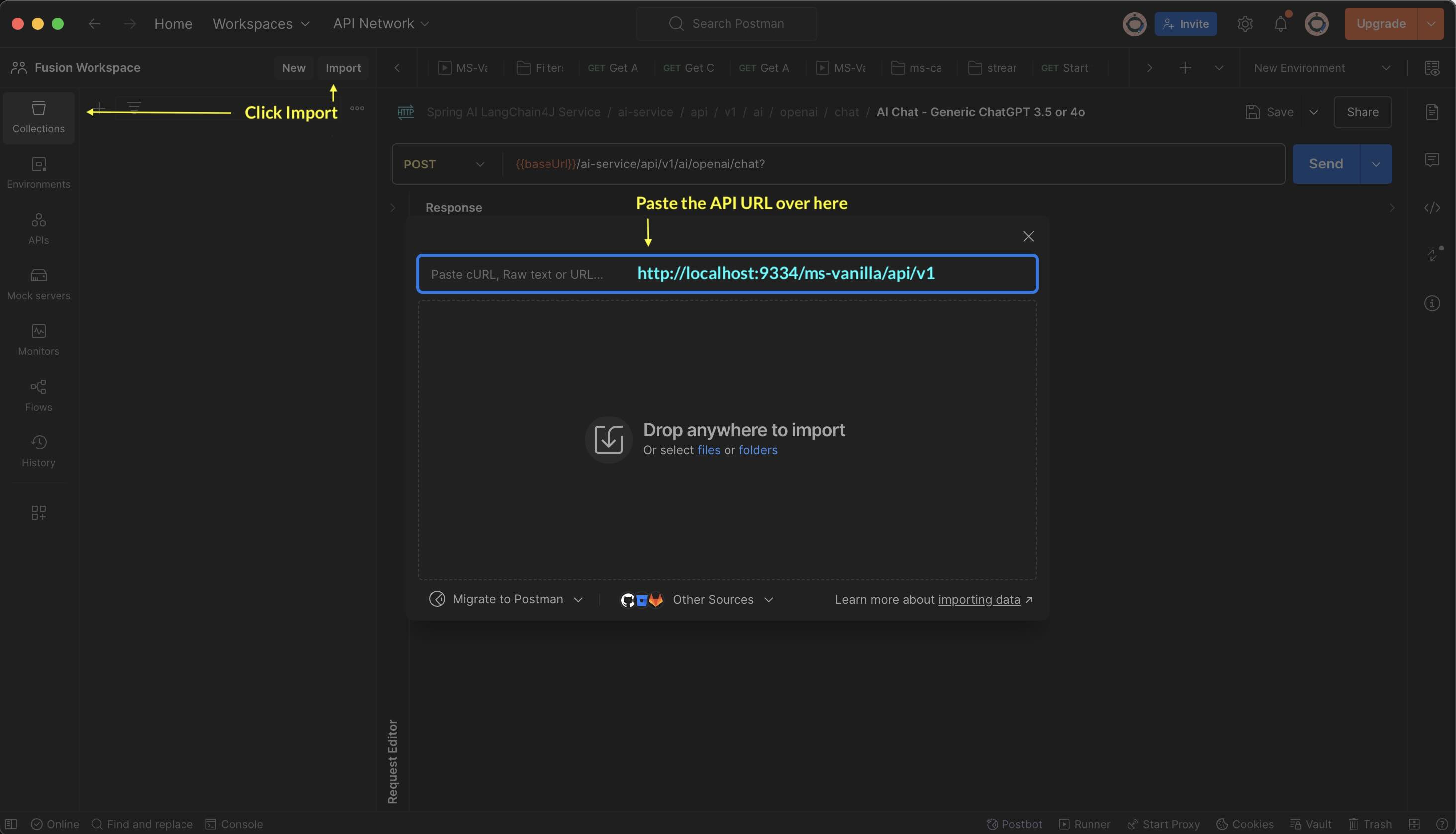
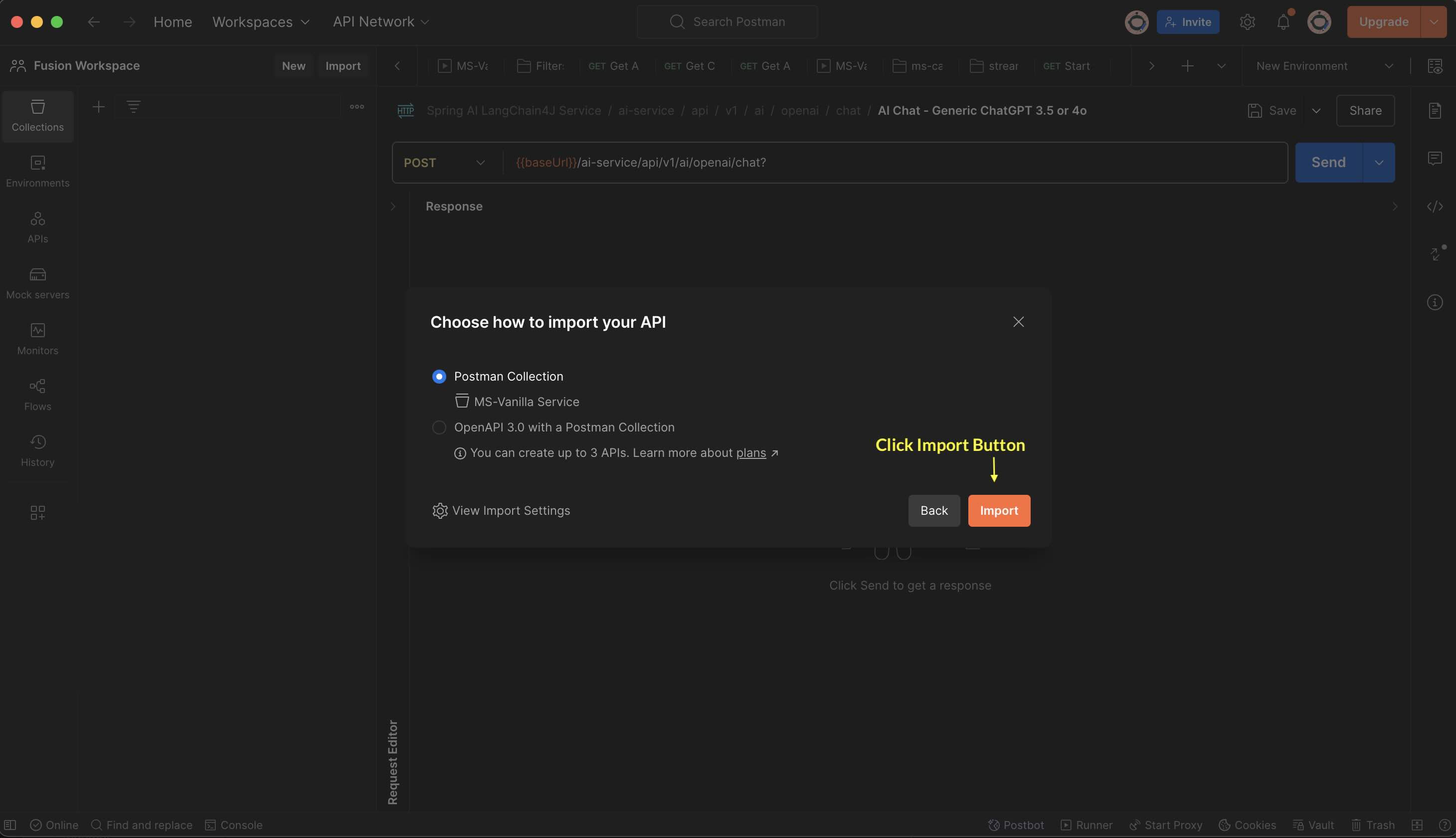
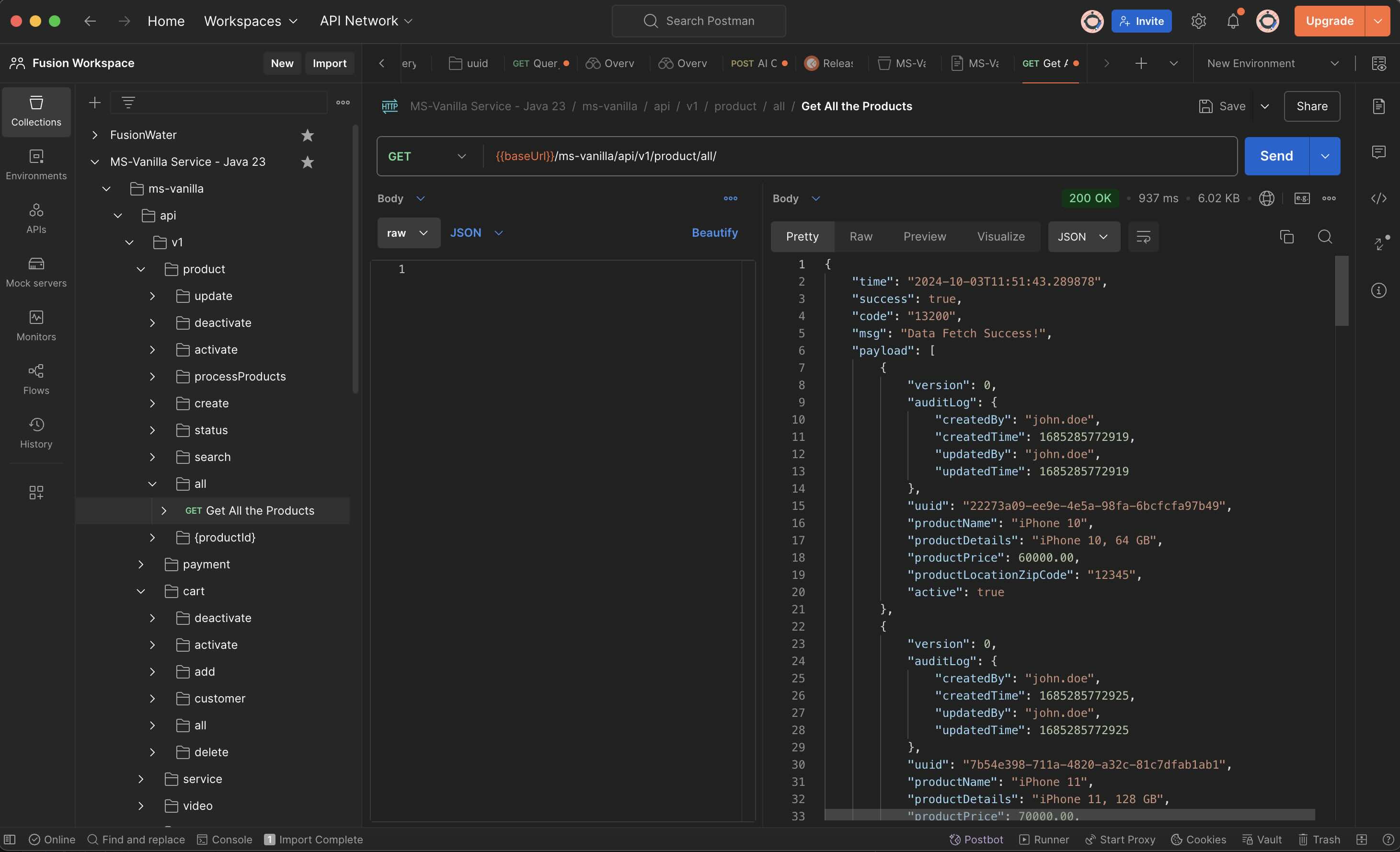
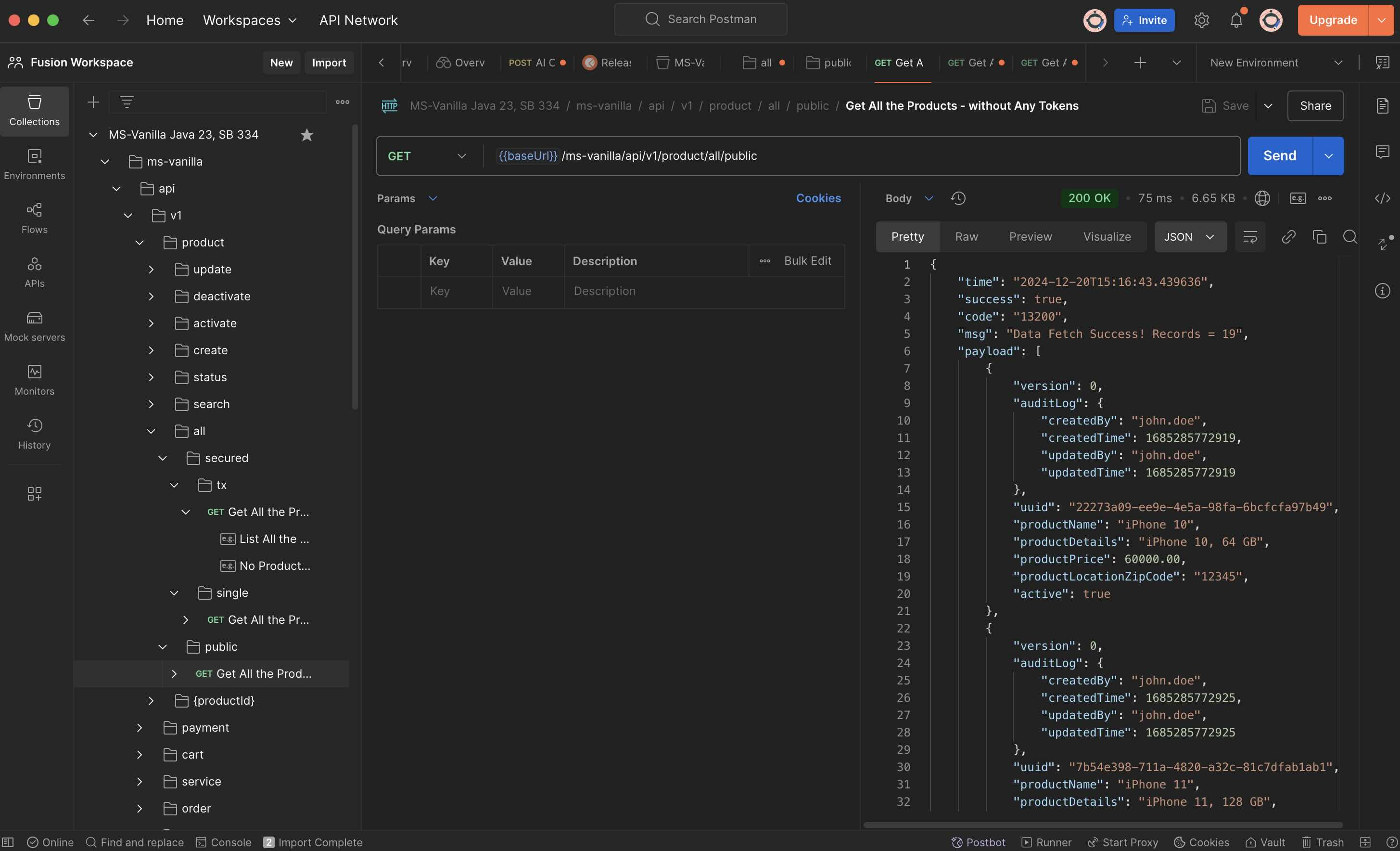
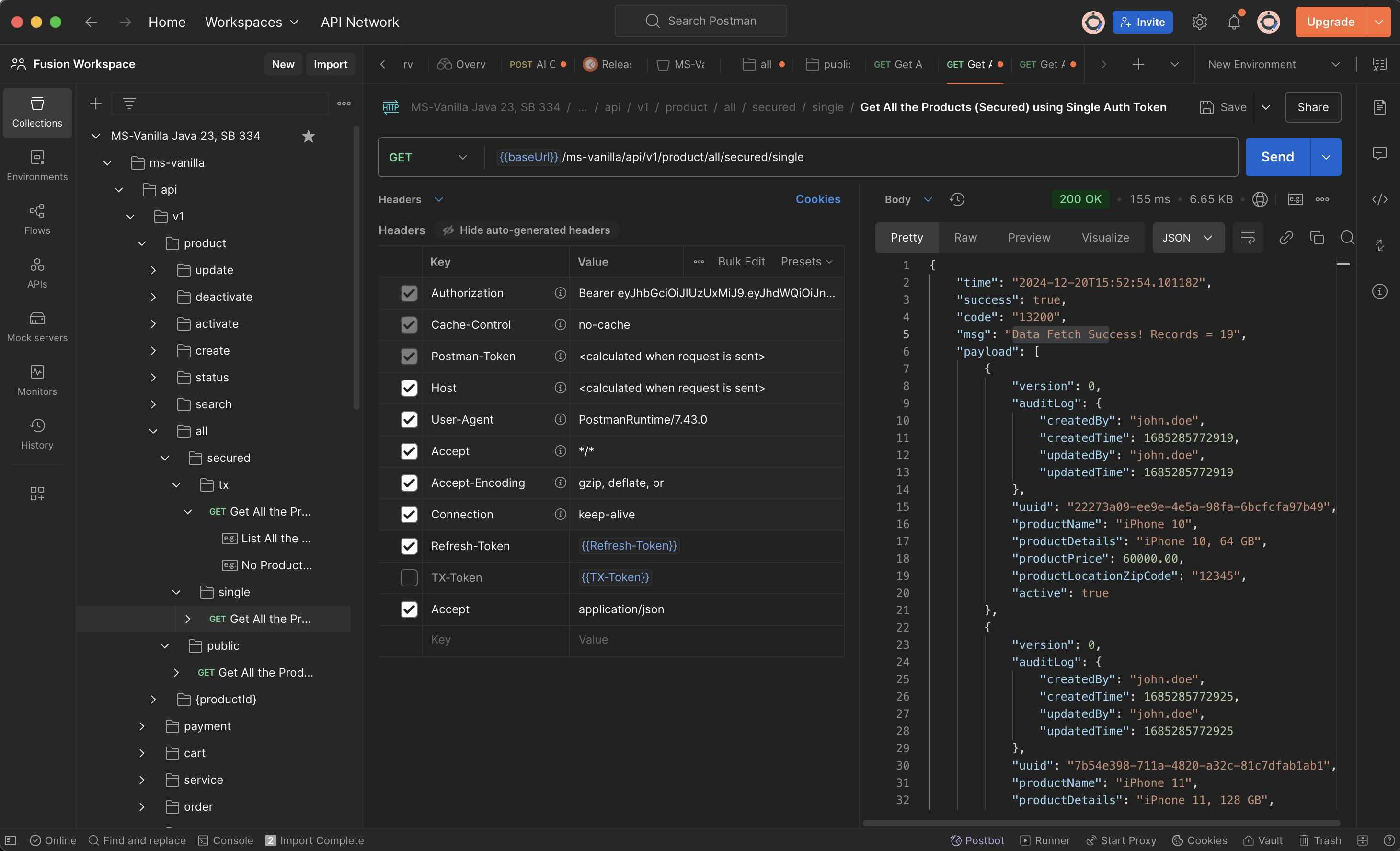
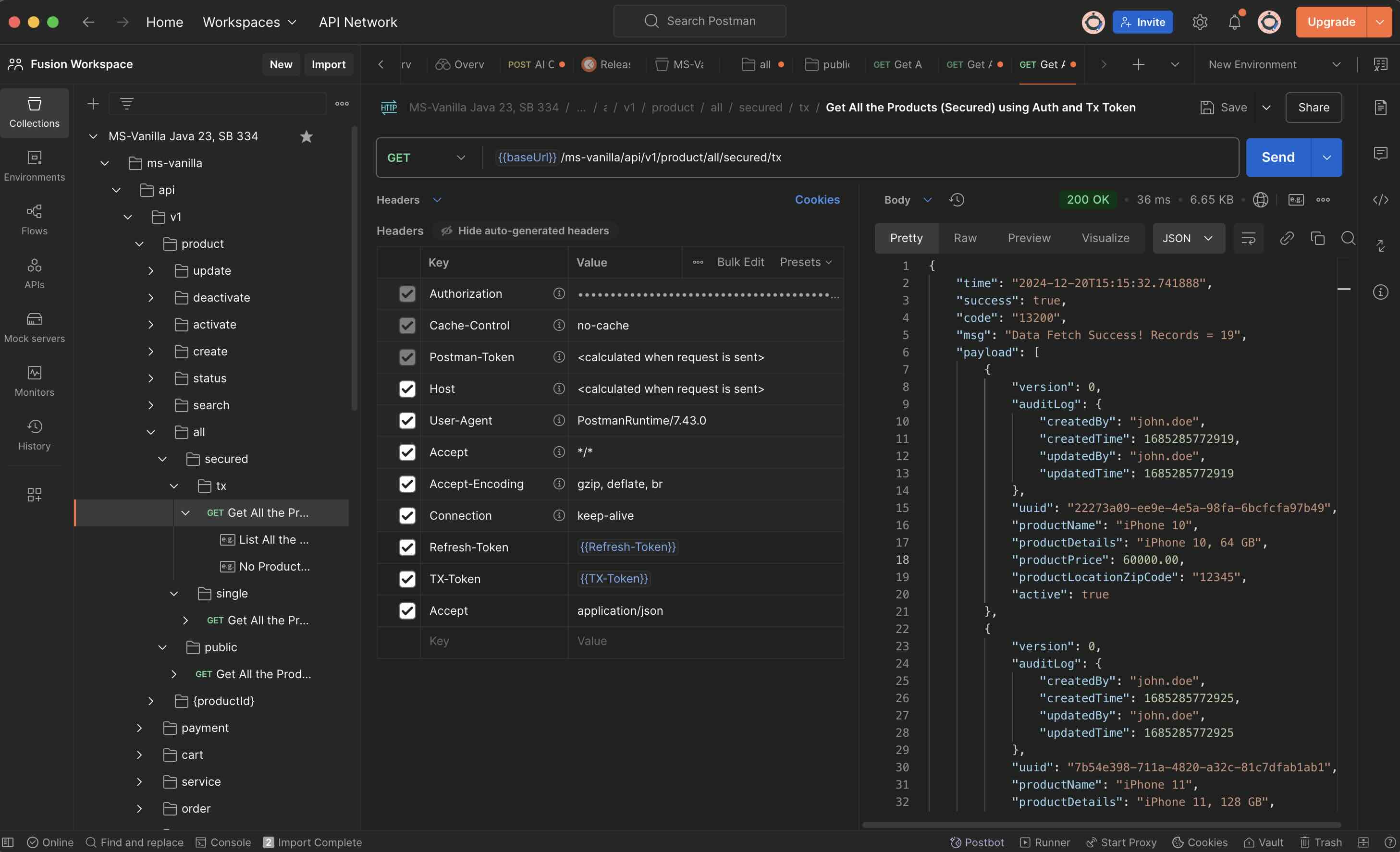
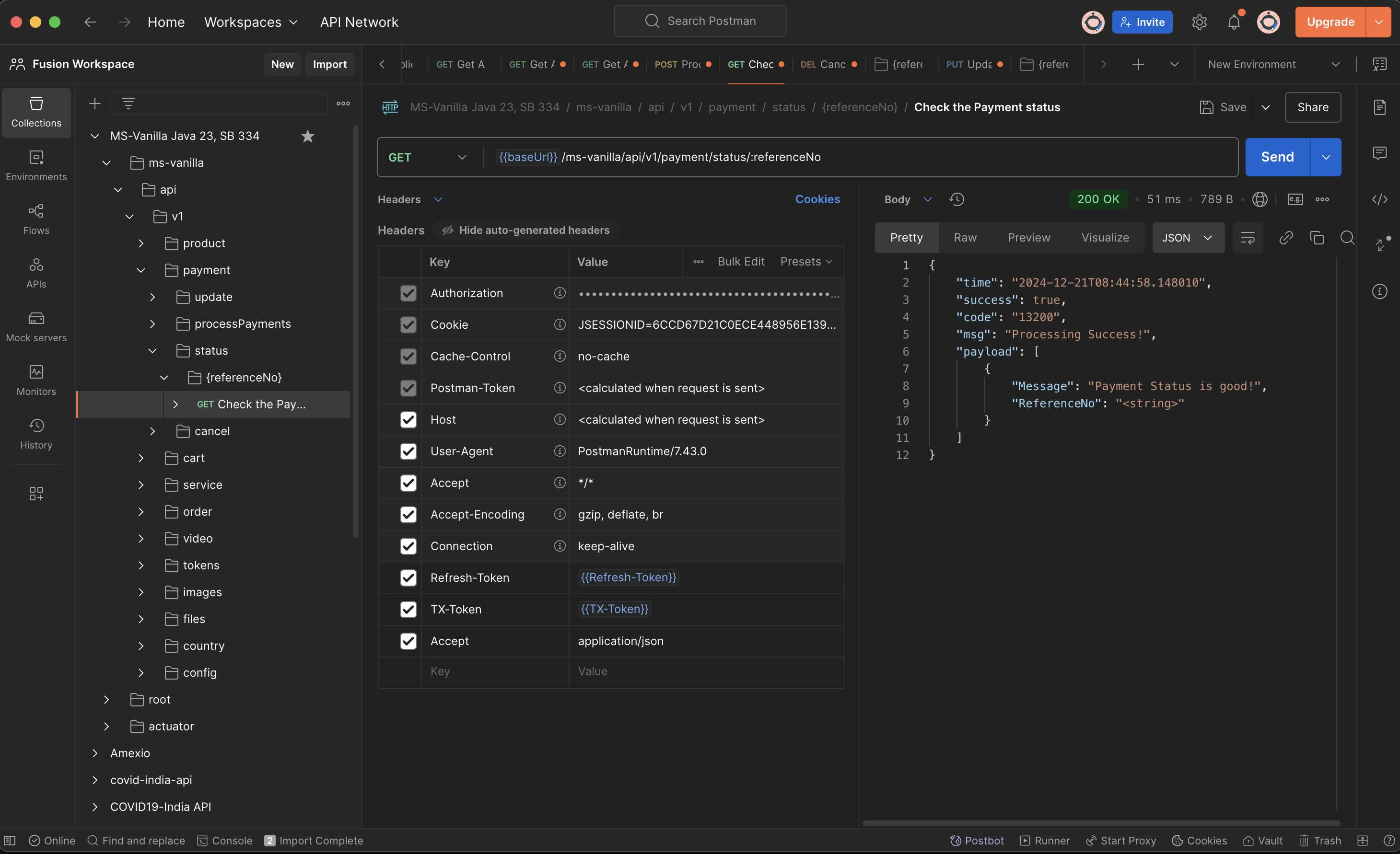
What is Postman?
- Postman is an API platform for building and using APIs. Postman simplifies each step of the API lifecycle and streamlines collaboration so you can create better APIs—faster.
- Download Postman for Windows, Mac & Linux. https://www.postman.com/
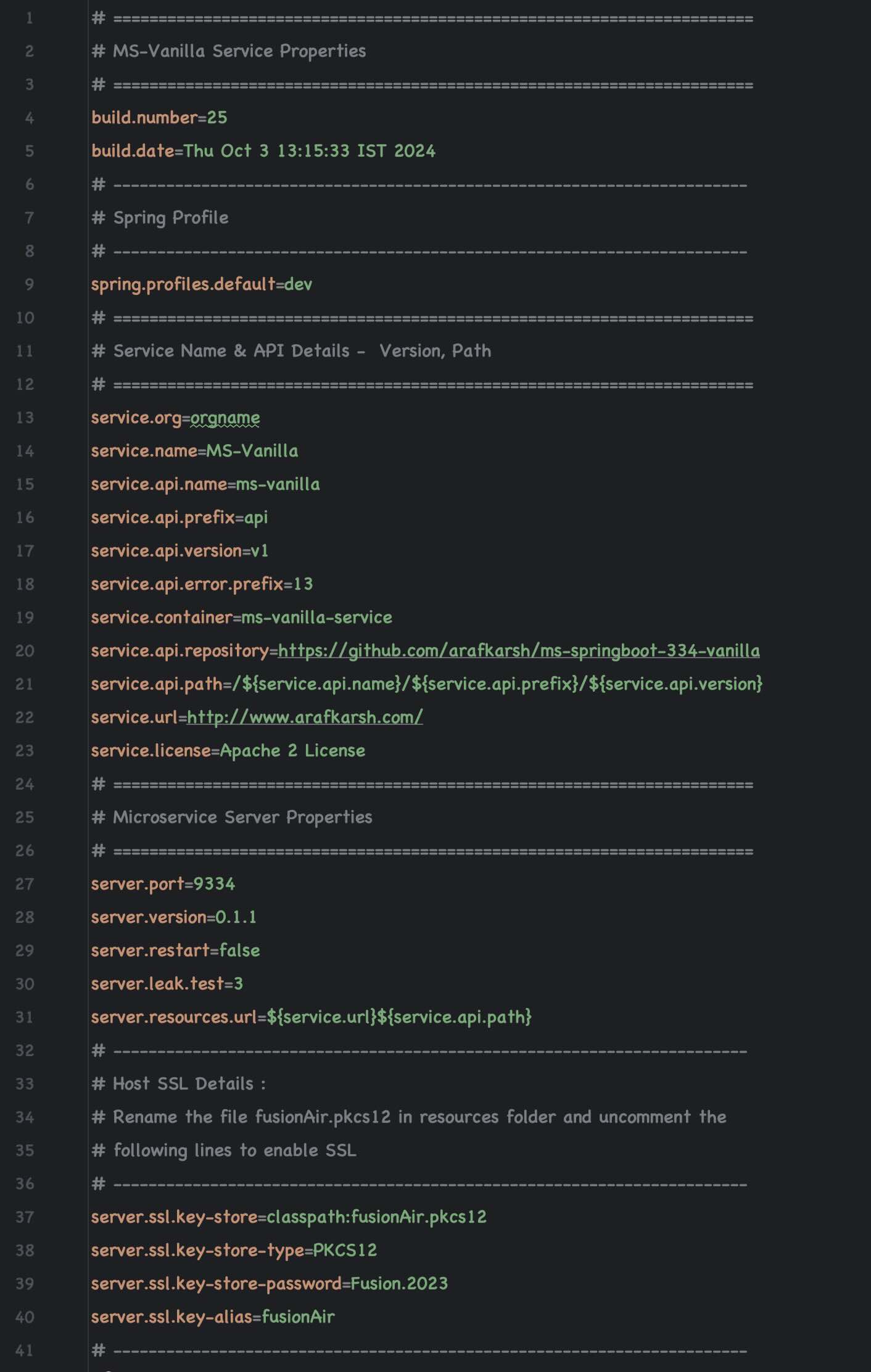
3. Configure the Template: Setup Org, Service, & Container Name, Versions, API Path in app.props.tmpl
- git clone https://github.com/arafkarsh/ms-springboot-334-vanilla.git
- cd ms-springboot-334-vanilla
Update the Properties Template
- Update the Org Name in src/main/resources/app.props.tmpl file (service.org)
- Update the Microservice name in src/main/resources/app.props.tmpl file (service.name)
- Update the API Version in src/main/resources/app.props.tmpl file (service.api.version)
- Update the API Name in src/main/resources/app.props.tmpl file (service.api.name)
- Update the Container Name in src/main/resources/app.props.tmpl file (service.container)
- Update the Server Version src/main/resources/app.props.tmpl file (server.version) Pom File 0.4.0 app.props.tmpl Microservice Server Properties server.version=0.4.0
When you change the version in POM.xml, update that info in src/main/resources/app.props.tmpl - server.version property also.
- Verify the Org Name in src/main/resources/app.props.tmpl file (service.org)
- Verify the container name in src/main/resources/app.props.tmpl file (service.container)
- Verify the microservice name in src/main/resources/app.props.tmpl file (service.api.name)
- build (Build the Container)
- scan (Scan the container vulnerabilities)
- start (Start the Container)
- logs (to view the container logs) - Wait for the Container to Startup
- Check the URL in a Browser
Update the Org Name in src/main/resources/app.props.tmpl file (service.org) Setup the Docker Hub or any other Container Registry
- push (Push the Container to Docker Hub)
- stop (Stop the Container)
- stats (show container stats)
(C) Copyright 2021-25 : Apache 2 License : Author: Araf Karsh Hamid
* Licensed under the Apache License, Version 2.0 (the "License"); * you may not use this file except in compliance with the License. * You may obtain a copy of the License at * * http://www.apache.org/licenses/LICENSE-2.0 * * Unless required by applicable law or agreed to in writing, software * distributed under the License is distributed on an "AS IS" BASIS, * WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. * See the License for the specific language governing permissions and * limitations under the License.